
Addressing Common Concerns of File Integrity Monitoring
There are some common concerns of File Integrity Monitoring that are worth addressing. Also called change monitoring, FIM is a security technique that uses a known baseline as a measure for verifying the current safety of an operating system and its software. Basically, it defines a safe “normal” and gauges current activity based on whether and how much it varies from that set standard. In considering using FIM, many security officers question (as they should) whether this method might be problematic. Would it register approved changes as threats? Would it overload systems with alerts whenever changes occur? But often these questions arise out of a lack of understanding of how FIM works. Here are some answers to a few common concerns of File Integrity Monitoring, and how running this security method through Microsoft’s Azure Security Center is a good practice to adopt.
Will FIM Confuse Acceptable Entities With Attacks?
In Azure Security Center, you decide what you want monitored through FIM. But don’t worry, you’re not all on your own. If you’re unsure of where to draw your lines, Security Center will recommend entities for you to monitor. Then you can accept, decline, or modify those recommendations as you see fit. Microsoft’s guide on what to monitor can help you get started. As a rule, exclude files that are frequently changed as a part of the normal work process at your company, so that FIM won’t flag them. More static files are the ones where FIM works best. If you do find yourself getting unnecessary alerts, you can easily edit your monitored entities.
How is FIM Data Managed Over Time?
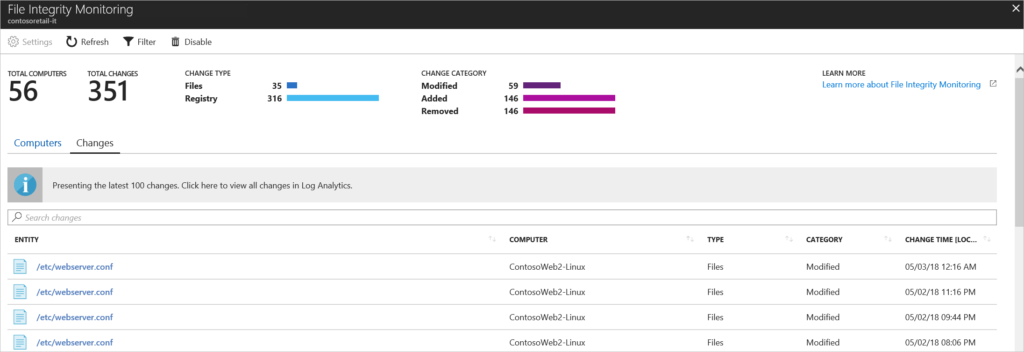
You can retrieve FIM data within Azure Security Center through Azure Log Analytics / ConfigurationChange. Once you pull up a data report, you can then export it to CSV for archival and/or channel it to a Power BI report if you wish. You also choose how much data you want to view and store. One of the filters in the FIM setup allows you to pick a time range to examine, and this can likewise be changed anytime.
Isn’t FIM Limited In What It Can Monitor?
Many people think that FIM can only monitor regular file systems. In fact, there are more areas where it can be of use. For example:
- Databases. Many aspects of a database could benefit from FIM monitoring, as a way for security admins to find out if unauthorized agents are getting access to it. You can keep default monitoring in place on more static databases, while monitoring custom parts of more active ones.
- Cloud storage. With widespread business cloud use, it makes sense for FIM to monitor files located in the cloud as well.
- Virtual machines. You can also monitor your virtual machines, using the host infrastructure as a base point.
- Network devices. FIM can additionally be helpful in keeping track of network devices such as routers, switches and firewalls. Abnormal changes among these devices can be indicative of threats as well.
- Active directory. Any element in Active Directory can be monitored with FIM. For instance, you might want to monitor users in restricted groups. This adds transparency to the changes that are made to directory services.
Closing Thoughts: Why FIM Is a Good Idea
One of the ways an attacker can gain control of a system’s resources is by targeting its files, a path that can often go undetected. Some zero-day attacks have no known signatures to look out for. Therefore, having information about any unauthorized changes that take place will put you in a better position to detect potential threats before they become serious incidents. Plus, under some regulations, FIM isn’t optional. To maintain compliance under standards such as PCI-DSS & ISO 17799, you must do File Integrity Monitoring.
To learn more about FIM and Azure Security Center, contact us. Setting up File Integration Monitoring for you is a change we’d definitely authorize.
For a different kind of take on baselines and what they mean for companies, check out our blog post on security poverty lines.
