
Blocking the Russian Hacker Group SEABORGIUM
As the war in Ukraine continues, now having reached six months since Russia’s invasion, cyber criminals in Russia are also persisting in their more longstanding digital efforts in key areas around the globe. For the past several years, Russian actors have aggressively interfered in the cyber space of Europe and the United States. One of the common tactics is social engineering, when hackers or their bots pose as legitimate email senders or account holders. Using fake personas, they attempt to engage or build a rapport with the targeted individual in order to gain trust and exploit vulnerability.
One of the threat actors aiming at people and organizations like this is identified as the Russian hacker group SEABORGIUM, also known (by overlapping indicators) as ColdRiver and TA446. It’s a hacker group believed to be state-sponsored and attempting to gain sensitive information of value to Russia. Microsoft’s Threat Intelligence Center has found SEABORGIUM running attack campaigns in NATO countries, and also in the Baltics, Nordics, and Eastern Europe, including Ukraine.
SEABORGIUM’s Objectives
Based on Microsoft’s tracking of the threat group since 2017, SEABORGIUM is closely aligned with the interests of the Russian state and appears to be more motivated by espionage than financial gain. Most of its targeting is on defense and intelligence consulting companies, non-governmental organizations (NGOs) and intergovernmental organizations (IGOs), think tanks, and higher education, as well as crucial individuals—intelligence officials and Russian citizens abroad, for example. As Microsoft points out, “intrusions have also been linked to hack-and-leak campaigns, where stolen and leaked data is used to shape narratives in targeted countries.”
Some of this targeting was aimed at Ukraine’s government sector leading up to Russia’s invasion there, but the malicious group is not limited to that endeavor and poses a much broader threat to governments, organizations, and individuals in many locations where information or the power to affect outcomes offer benefits for Russia.

How the Russian Hacker Group SEABORGIUM Operates
The group gains trust through consistent social engineering tactics, conducting reconnaissance of targets and personalizing emails in order to sound realistic. They use social media as well as directories and open-source intelligence to gain information about the target and their circle of contacts. Then they generally impersonate one of the target’s acquaintances, often using a newly registered account very similar to an authentic one. Over multiple emails, they build trust and create a sense of familiarity, finally including a malicious attachment once they’ve gotten positive responses. For example, one documented phishing scam with the subject “Wondering what you guys think” builds curiosity and—after a request from the recipient—sends the attachment.
Another method SEABORGIUM uses is an ironic claim of cybersecurity protection for an organization, supposedly from its own security team. The example below warns about active hacker groups and provides a .pdf for employee awareness of harmful activity.
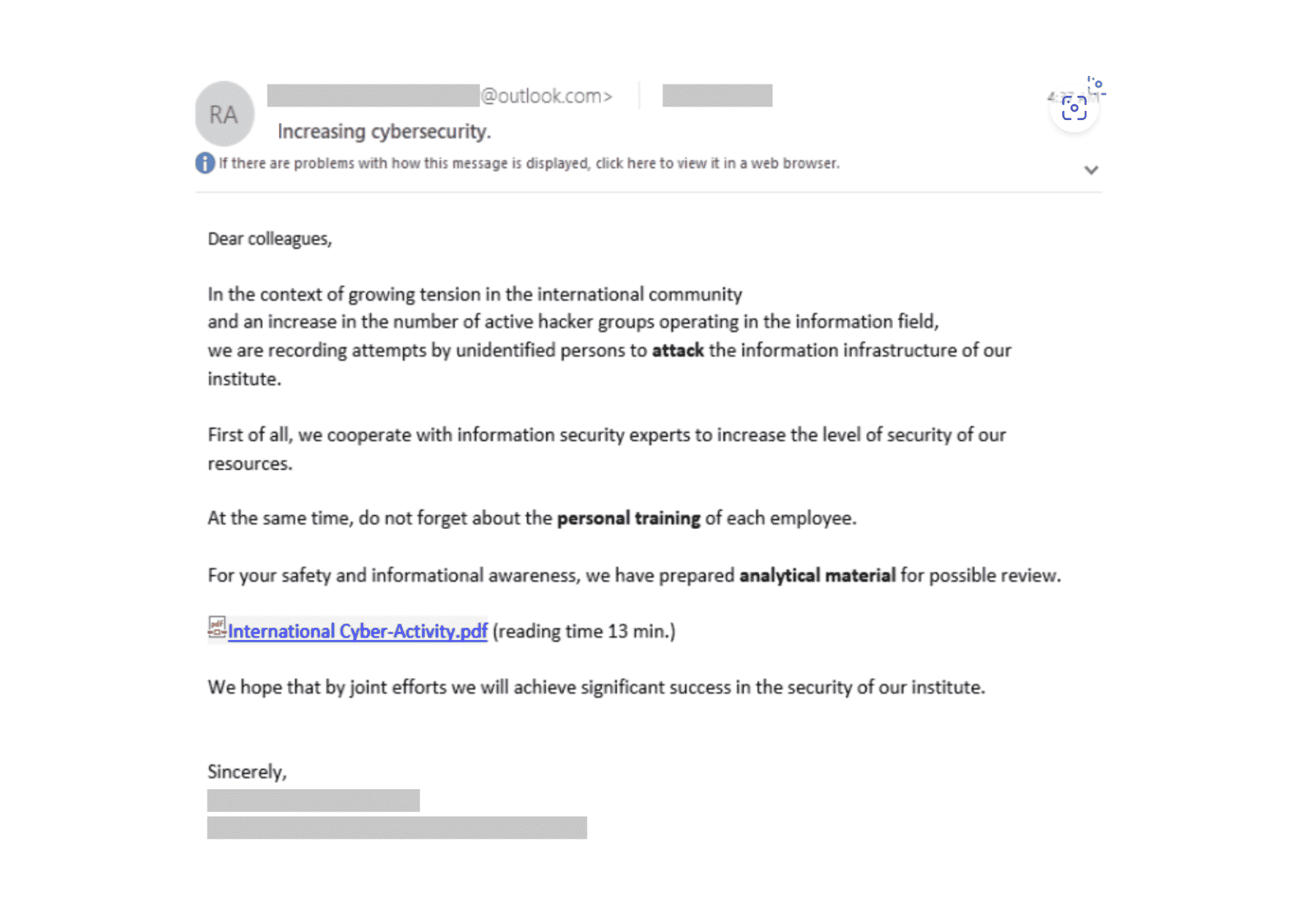
Once the recipient clicks on a harmful link or document, they’re directed to a phishing framework and asked for authentication, allowing for their credentials to be stolen. Once this access has been obtained, the hacker group will steal documents, exfiltrate intelligence data, or set up persistent data collection. It also gives them the opportunity to further impersonate and engage with people of interest in order to gain more information.
Stopping Malicious Campaigns
With help from Google’s Threat Analysis Group (TAG) and the Proofpoint Threat Research Team, Microsoft has tracked and disrupted SEABORGIUM’s efforts and acted to block their attack pathways. When the threat group’s social engineering has taken place through their services, they’ve disabled the respective accounts and notified affected customers. Microsoft Defender SmartScreen has also set up detections against the phishing domains associated with SEABORGIUM’s activities.
As an organization, it’s always helpful to make sure you have spam and malware blocked, and to use mutli-factor authentication (MFA) and implementations like FIDO tokens for additional security. For more tips to avoid falling prey to threat actors like SEABORGIUM (as well as other social engineering hackers), see this advisory report from the Microsoft Threat Intelligence Center.
