
Introducing Our Compliance Accelerators
Are you concerned with new compliance regulations or the wave of news around data breaches? These issues are pressing concerns for businesses today. With so much data collected online, data privacy is an important area to be mindful of and manage properly. This is not only ethical good practice, it’s also necessary for various compliance laws. Maintaining strong information governance and good compliance standing can help companies save a lot of time and money that would be lost in the event of a harmful data breach, too. We know that taking care of these issues can be daunting for organizations, so we’re here to help accelerate your compliance and governance adoption with a series of four Compliance Accelerators.
What Are Compliance Accelerators?
Mention “Compliance” and most people and company teams share an internal groan. They think: compliance with what? Where to start? What to cover? How long will this take? How much will it cost? That’s why we’ve developed Compliance Accelerators—to provide quick time-to-value in addressing this issue for organizations of all sizes.
Infused Innovations has developed these four Accelerators with particular regard for our small and medium-sized business clients, wherever they may be on their compliance journey. SMBs are subject to current and coming information protection legislation and regulations, and they are often at a greater risk of non-compliance than larger enterprises.
Our Accelerators are a culmination of best practices for Information Governance throughout a Microsoft environment, and they progress along a compliance maturity model with each one building upon the last. These can be leveraged as a packaged series or as ad-hoc offerings to clients at different stages in their compliance maturity progression. Organizations that have already set up an Information Governance Strategy but would like help proceeding with Privacy, for example, could start with the third Accelerator—Manage Regulatory Compliance and Privacy.
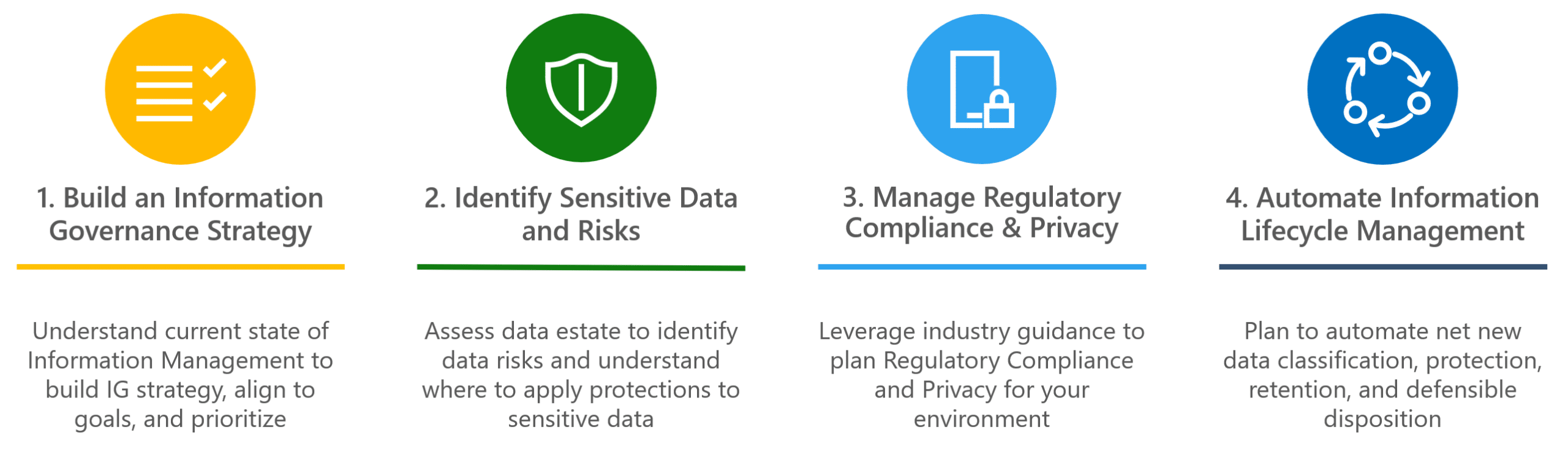
The compliance maturity progression is made up of four consecutive steps, each of which is addressed with one Accelerator:
- Build an Information Governance Strategy: Starting out on the right track involves building a comprehensive strategy to lay the foundation for a smoothly running information management system. We’ll work with you to define your Governance Strategy, align it to your business objectives, understand your prioritization needs, and help define the goals to compliance.
- Identify Sensitive Data and Risks: In order for risks to be addressed, we’ll help you first identify and understand the sensitive data that your organization handles. This visibility becomes critical for successful management.
- Manage Regulatory Compliance & Privacy: Here’s where our experts will leverage your information discoveries, along with our Regulatory Compliance and Privacy expertise, to assess your current environment’s alignment with those requirements. We’ll identify any gaps, prioritize them, and provide an assessment plan and action items to address. Whatever your industry or business type, we can help you understand your current compliance posture and work toward addressing issues.
- Automate Information Lifecycle Management: Finally, we’ll help you create a plan to automate your information lifecycle: from understanding types of information, to sensitivity labelling and data loss protection, to retention and disposition. Automation helps significantly reduce administrative burden, but in a rapidly changing world, even automation requires a bit more than “set it and forget it.” We’ll help you build in reviews and updates to keep your ILM efforts consistent, scalable, and adaptable.

More About Our Accelerators
Our suite of Compliance Accelerators listed here also provides a segue into our Zero Trust Security Accelerators, which can be used to build and deploy a best-practice Zero Trust Strategy. In today’s digital landscape with threats coming from all directions, Zero Trust is the best and strongest security approach for an organization to take.
All of the Infused Innovations Accelerators are designed to give clients a smooth process with quick time-to-value, so that other aspects of their business can keep running productively.
Over the next few weeks, you’ll see blog entries that dive into each one of the Compliance Accelerators in a little more detail. In the meantime, reach out to see how we can help your company’s governance strategy!
–
By Kristi Robison and K.K. Tucker

What a great offering! And steeped in the reality of what faces businesses. There is so much to know, and muchly depends on knowing what is required and what is possible. Lots of food for thought. Thank you!