By now, we know it well: cyber threats are a major concern with great potential for damage. There are so many different ways that adversarial actors can gain access and cause breaches to networks, devices, and organizations. MITRE ATT&CK is a structured breakdown of the techniques that cyber attackers use, as well as a catalogue for discussing and tracking those actions. By surveying the matrix charts of the ATT&CK framework, defenders can gain substantial insights into attack paths and mitigation possibilities. They can label and track breaches that do occur in order to better understand weaknesses. As the only framework that compiles malicious cyber behaviors in such a systemized and visual way, MITRE ATT&CK is an enormous tool for cybersecurity.
A Framework for Understanding Cyber Crime
It may look like “ATT&CK” is a relevant word with a lookalike symbol inserted as a substitute for a letter, like people sometimes use for their passwords (a nice effort, but still vulnerable: see the Brute Force technique). While that may be the case, it’s actually an acronym, short for Adversarial Tactics, Techniques & Common Knowledge. The government-supported cybersecurity corporation MITRE first created the ATT&CK chart in 2013 to compile and organize known attacker actions. This allowed for a whole new perception into the world of malicious cyber behavior. (Previously, defenders were mainly just looking at IP addresses and domain names.) It created a roadmap for organizations to see where they stand in terms of vulnerability to particular maneuvers, and it categorized the mess of cyber crime into a neat and handy chart with a common language that could be shared across industries.
The Elements of an ATT&CK Matrix
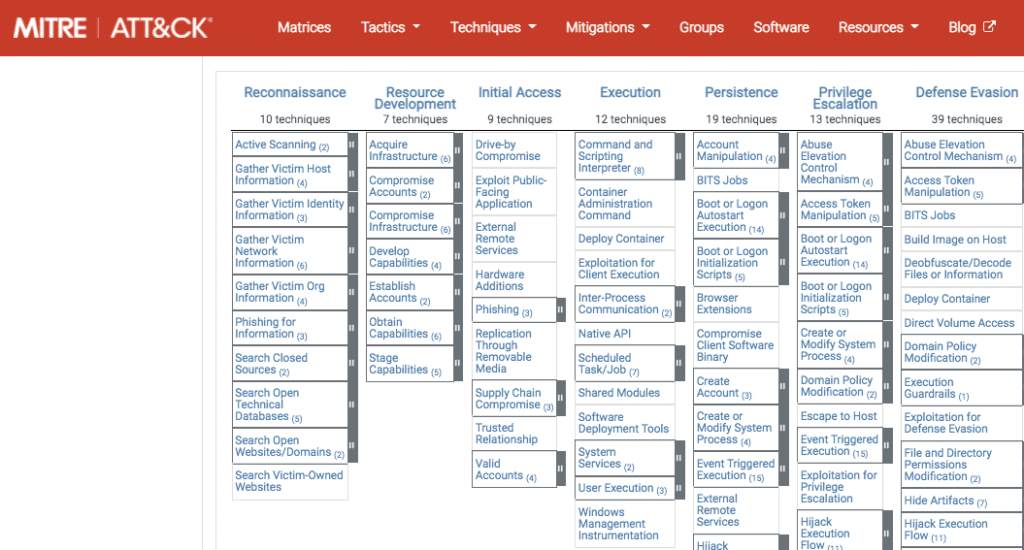
MITRE ATT&CK matrices listed with an example of tactics and techniques in the Enterprise matrix
The ATT&CK framework covers Enterprise and Mobile environments, which are broken down into different operating systems and cloud locations. There’s a matrix that pertains to each one. In any given matrix, the tactics are listed across the top of each column, representing the aims of an attack or part thereof (Reconnaissance, Resource Development, etc.). Then, listed down the columns are the specific techniques that attackers go through in order to achieve those aims. If you click on any of the techniques in the matrix, you see an explanation of what the technique does (along with any sub-techniques), examples, mitigations, and detection. Each technique is also tagged with an ID and other relevant information. This standardized and structured compilation gives cybersecurity professionals a common language with which to describe and document attacks, and it helps build up an informed defense against them.
Example of information about an attack technique
Another insightful resource is the Groups page, which indexes and describes dozens of known adversarial groups around the world.
Applications for MITRE ATT&CK
Anyone who’s interested can access this extensive knowledge graph for free. Its usefulness spans the range of informing, communicating, tracking, testing, and responding. Mapping an organization’s defenses to ATT&CK can highlight security gaps and help defenders continually improve. These applications are utilized by both government intelligence and the private sector, creating a uniform foundation for cybersecurity professionals in any industry to build defense strategies and mechanisms.
What’s Necessary to Make the Best Use of MITRE ATT&CK?
While the ATT&CK framework provides unrivaled insights into attack methods, that doesn’t mean it’s without limitations. It’s important to remember that this index is based on known, real attacks—so there are potential actions that adversaries could do as they continue to learn and evolve, which aren’t listed in ATT&CK. Also, techniques can be executed in a variety of ways, so detecting and blocking one route can leave security teams with a false confidence in their protection against that tactic. In any case, organizations won’t make the most of MITRE ATT&CK without mapping a defense solution to its framework. This can be done manually or through automated approaches, or ideally as a combination of both. The level to which an organization is able to map to ATT&CK’s details will determine the extent of its value.
An exciting complement to ATT&CK published this year is MITRE D3FEND, which similarly outlines defensive techniques against infiltrations. Read more about that here.