Posts Tagged ‘Cybersecurity’
Azure Firewall Basic Geared Towards Small and Medium Sized Businesses
Firewalls have long been a first line of defense for network security. The barrier that they create between internal and external networks acts as a sort of living fortress wall, monitoring the traffic and deciding what to let in. A firewall can take the form of hardware or software—and in the case of Azure Firewall,…
Read MoreMicrosoft Defender for Endpoint and Intel TDT Combine for a New Ransomware Defense
Ransomware continues to be a growing and evolving threat. As some cyber attackers become increasingly sophisticated, things like ransomware kits allow even hackers with a low level of skill to take part in this malicious activity. With relatively little investment, they end up reaping big gains. And once that happens, they have all the more…
Read MoreFacts and Misconceptions About Zero Trust
Cybercrime reports have gone up over 300% in the last couple years. And a surprisingly large number of breaches happen with company employees involved, often because of mistakes like falling for phishing baits. Any insider in the company can potentially be a point of vulnerability that can expose the whole network. That’s why a Zero…
Read MoreCyberattacks in 2021 Doubled Those of 2020
If 2020 was the year of Covid chaos, 2021 was the year of cybercrime explosion. Of course, both of these roller-coaster years were much more complicated and neither can be summed up in one simple term like that. But it’s true that cyberattacks have risen dramatically this year, making even 2020 look tame in comparison.…
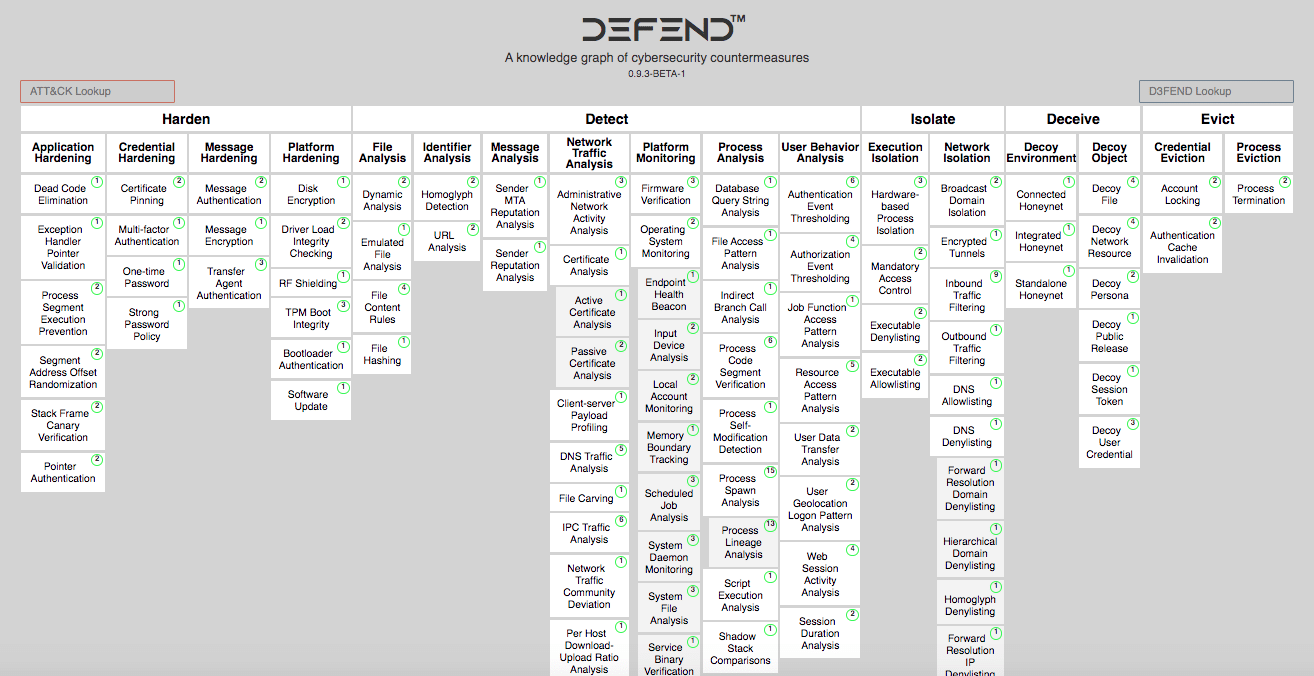
Read MoreMITRE D3FEND and Azure Mappings: Counteracting ATT&CK Methods
Whenever I read about MITRE ATT&CK and D3FEND, a part of my brain goes, “Wh@t?” But another part is excited about such a comprehensive reference framework to nail down the moves that cyber attackers make—and to map responsive counteractions in defense. With funding from the NSA, MITRE D3FEND was released this summer to fill in…
Read More10 Cybersecurity Stats You Need to Know
Cyber attackers are smart, capable, and only becoming more so as time goes on. With increased vulnerability from public health fears and shuffled work settings, individuals and companies have suffered a great deal of attacks in the last couple years. And that’s on top of what was already a teeming problem. Some of the numbers…
Read MoreWhat is Content Disarm and Reconstruction (CDR)?
Much of cybersecurity depends on detection—like the detection & response solutions we’ve written about recently. But there’s another, less common way to approach malware threats. Content Disarm and Reconstruction, or CDR, strips down a file’s active content and rebuilds the file with only known, safe elements. Sometimes called file sanitization, CDR delivers a clean, “sanitized”…
Read MoreMicrosoft 365 XDR
Disclaimer: It’s not actually called Microsoft 365 XDR. (But a lot of people like to type that into a search engine.) MD XDR encompasses the entire security suite while the M365 security suite is referred to as Microsoft 365 Defender. We agree with you–it’s just as confusing as the prior ATP product names. Extended Detection…
Read MoreWhat Are the Differences Between MDR, EDR and XDR for Cybersecurity?
You may have been hearing about XDR in recent months—this is a rising technology that improves upon MDR and EDR, which themselves are great advancements from older solutions. Gartner predicts that the majority of enterprises will have replaced legacy security software with one of these advanced solutions by 2023. So what do all these offerings…
Read MoreXDR Pioneers and Leaders
One of the strongest cybersecurity offerings today is Extended Detection and Response, or XDR. It combines and centralizes security data from several sources: Security Information and Event Management (SIEM); Security Orchestration, Automation and Response (SOAR); Endpoint Detection and Response (EDR); and Network Traffic Analysis (NTA). Because these elements are all working together, visibility and and…
Read More