Secure Modern Workplace
The Difference Between an MSP, MSSP, and SSP: Choosing the Right Service Provider for Your Business
In the ever-evolving world of technology and business strategy, organizations often seek external support to enhance their operations. Managed Services Providers (MSPs) and Managed Security Services Providers (MSSPs) are a common and popular choice, but for many organizations Strategic Services Providers (SSPs) can be a better fit. Understanding the differences between these two service providers…
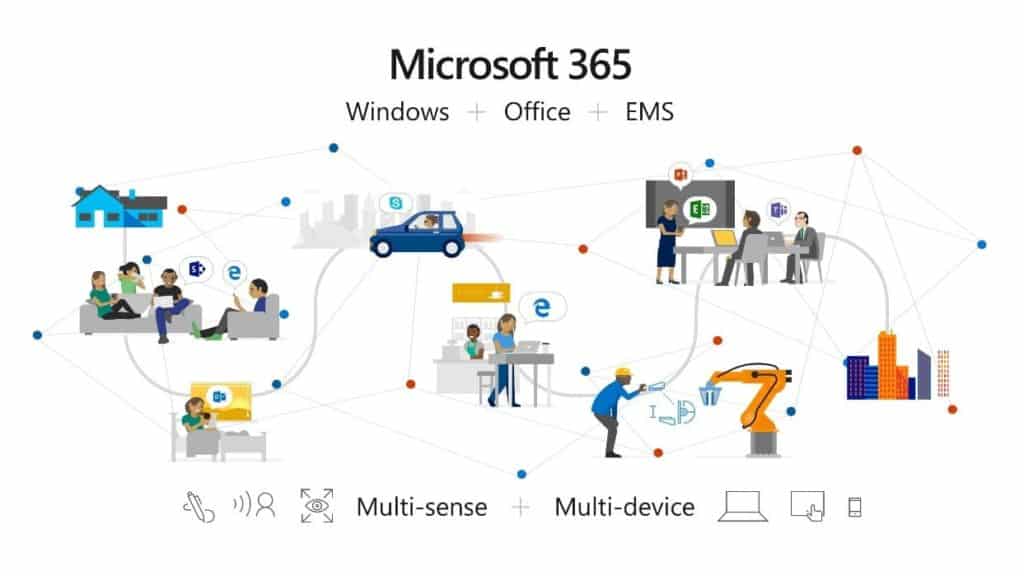
Read MoreThe Complete Office 365 and Microsoft 365 Licensing Comparison
Full Microsoft 365 licensing comparison matrix of subscriptions that includes features and pricing for Office 365, EMS and Windows 10 Enterprise plans.
Read MoreThe Workplace Is Changing — Are You Ready?
The Workplace Is Changing. Are You Ready? A couple of months ago, I wrote about the “New Normal” and how technology is being reimagined for hybrid work. Since that time, there have been starts and stops with corporations hoping to get people back to the office by September. As we all know, globally the various COVID…
Read MoreSecurity Poverty Lines
When we think of the term “security poverty lines,” we rarely think of organizations’ abilities to maintain good hardware and cybersecurity. Yet this is a largely unrecognized problem for many of today’s companies. In a podcast on Security Nation, head of of advisory CISO services at Duo Security Wendy Nather discusses the problem of the…
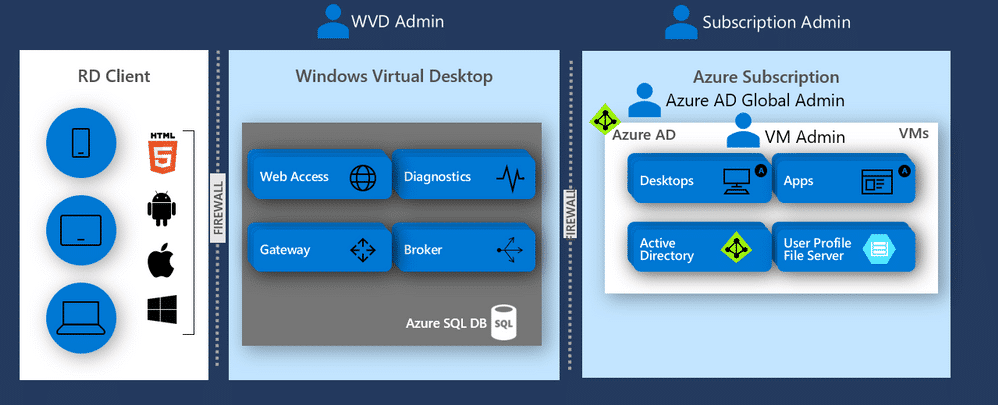
Read MoreStep-by-Step Guide to Install FSLogix on WVD
With the recent GA of Windows Virtual Desktop (WVD) Microsoft has extended its ability to deliver important endpoint capabilities to users anywhere in the world. Designed to improve upon the standard Windows Virtual Desktop capabilities, installing FSLogix on WVD can enhance and simplify these sorts of non-persistent environments. Benefits of Installing FSLogix on WVD Maintain…
Read MoreMicrosoft Ignite 2019’s Top Announcements
Microsoft Ignite is the annual conference where the tech giant gets to show off its exciting new developments. The company’s many announcements are of interest to IT professionals, developers, and big Microsoft fans. We love hearing about new streamlined improvements and innovative previews offered. This year’s conference seemed to present more news than ever—Microsoft provided…
Read MoreWindows Autopilot for Workstation Imaging
The typical process of acquiring new devices and configuring them for company use is a bit of a headache. It goes something like this: your IT admin gets the devices, wipes them of their default settings, re-images them with custom images using Ghost or Acronis, obtains drivers, configures the relevant applications and settings, and finally…
Read MoreMicrosoft 365 Plans for Education
Educational institutions face the cybersecurity risks of other organizations and more. Because of certain factors inherent to the nature of educational places, these institutions are at a greater security risk. Limited budgets, privacy concerns, intellectual property, and specific compliance regulations create an atmosphere that’s different from most organizations. The multiplicity of college departments makes for…
Read MoreCybersecurity Automation with Azure Sentinel for SIEM and SOAR
Traditional security operations centers could get away with pre-set prevention technology and detection mechanisms based on prior knowledge of attack methods. But in the past few years threats have developed rapidly in both number and sophistication. It’s no longer enough to look at intelligence as a one-way product addressing occasional threats. Moreover, not all threats…
Read MoreA Guide to Ransomware Protection with Microsoft 365
Protecting modern IT systems from ransomware is fairly simple now with Microsoft 365. Microsoft uses AI models and machine learning to process 6.5 trillion daily signals with a team of 3,500+ full-time security engineers that invest $1 billion annually in R&D. To put that in perspective, a managed SOC like Arctic Wolf processes “only” 20…
Read More