Step-by-Step Guide to Deploy Microsoft Sentinel
Note to readers: this guide was created in 2019 and is being kept online as an example of the process. The product (now Microsoft Sentinel) has evolved over the years, and a well-built, best-practice deployment is not a "15 minute guide" level of effort. Please reach out to us if you're interested in using Sentinel to monitor signals from all over your organization, users, devices, data, applications, and more...
Azure Sentinel is by far the most exciting announcement out of Redmond so far this year. Aside from that, what is Azure Sentinel? It's a 100% cloud based Security Information Event Management (SIEM) solution. I've been referring to Log Analytics with Azure Security Center as Microsoft's cloud SIEM solution for a couple years, but Azure Sentinel allows you to collect logs from anywhere. ANYWHERE. When you deploy Azure Sentinel, anything that ships Common Event Format (CEF) logs over port 514 can integrate with Azure Sentinel. Even more exciting is the one-click setup for a number of data connectors:

What is Security Information Event Management (SIEM)?
Think about your one friend that has memorized every line from every Marvel movie. And now think about every time he corrects you when you misquote the movie or mistake which movie a specific scene was from. It's that, but for your hybrid cloud network. Your friend knows what to expect and he throws an exception when something is out of place.
Every time you sign into Outlook, an audit log is generated. Any time you share a file in OneDrive, a log is generated. When you connect your personal phone to the corporate network, a log is generated. If your frustrated senior IT engineer tries to download all of your intellectual property from Teams and then deploy EternalBlue to the entire network, then a LOT of logs are generated. SIEM collects all of those logs and uses trained machine learning models to generate risk profiles for users and devices on your network based on expected behavior.
So when unusual behavior occurs, like stealing your IP, an alert is generated and Microsoft Cloud App Security with Azure Logic Apps can be used to automatically block the download and lock the user out of your tenant. If a user logs in from Italy 30 minutes after they left the office in Boston, the login can be automatically blocked.
Digital forensics and breach investigation
SIEM also provides the digital forensics that allow you to investigate the attack chain of a breach in its entirety. With Microsoft analyzing 6.5 trillion signals daily, they have the largest security dataset of any company in the world. Even more data points than your friend that's watching the Avengers Endgame for the fifth time as we speak.
To get the full value out of Azure Sentinel for your Microsoft 365 environment, you need EM+S E5, M365 E5 or something similar to collect telemetry from MCAS and AADP2. As with all Microsoft products, you can review our blog on Microsoft 365 subscription licenses to make sure you have access to all the security products discussed in this post.
Deploy Azure Sentinel in 5 Minutes
If you already have Log Analytics and Azure Security Center deployed, as all of our customers do, it takes 5 minutes to deploy Azure Sentinel. However, if you don't have those services setup yet, it might take you 15 minutes to deploy. Before we jump into configuring data connectors and dashboards, let's get go through the prerequisites quickly.
Prerequisites: Configuring Log Analytics and Azure Security Center
Our engineers will gladly assist you through customizing Log Analytics deployments for your environment, but let's just create a workspace for demonstration purposes.
- Navigate to the Log Analytics blade in the Azure Portal
- Click Add and complete the form to create a new Log Analytics Workspace. (Note: Refer to the Azure Sentinel documentation to make sure Sentinel is available in your region.)

- Now let's head over to Azure Security Center and Enable it.

- Next, go to Security Policy and click Edit Settings for your subscription name:

- Configure Security Center to Use another workspace and select your Log Analytics workspace.
Optional: Turn on Auto Provisioning (this will cost you $15/mo per VM plus any data overages)

- Next, go to Threat Detection and enable Microsoft Cloud App Security and Microsoft Defender ATP integration:

That's it! You've finished setting up all the prerequisites to deploy Azure Sentinel.
Disclaimer:
Infused Innovations does not recommend deploying Azure Security Center with only these configurations in production environments. This is the minimal configuration to deploy Sentinel. It is important to tune Azure Security Center policies and alerts to meet your organization's specific regulatory requirements. The out-of-box configuration of Azure Security Center is not sufficient for most organizations, but does provide immediate insights to your environment.
Deploy Azure Sentinel
Now for the easy part.
- Login to https://portal.azure.com click All Services and search for Azure Sentinel
- Click the Connect Workspace button

- Next, link your Log Analytics workspace:

That's it. You just deployed Azure Sentinel. But it's useless without data, so let's click Collect Data:

Almost all of the Microsoft data sources can be enabled with 1-4 clicks.
Deploy Fusion for Azure Sentinel
UPDATE 9/2019: Fusion is enabled by default in all new deployments and you can skip this step!
Now that you're ingesting data into Azure Sentinel, let's enable Fusion. Fusion for Azure Sentinel uses ML to help reduce alert fatigue and false positives. Fully utilizing the Microsoft Intelligent Security Graph to correlate millions of low-fidelity signals for unusual behavior across the entire Microsoft ecosystem, Fusion attempts to reduce the amount of security cases to investigate.
To enable Fusion for Azure Sentinel, open the Cloud Shell in the Azure Portal and enter the following command:
az resource update --ids /subscriptions/{Subscription Guid}/resourceGroups/{Log analytics resource Group Name}/providers/Microsoft.OperationalInsights/workspaces/{Log analytics workspace Name}/providers/Microsoft.SecurityInsights/settings/Fusion --api-version 2019-01-01-preview --set properties.IsEnabled=true --subscription "{Subscription Guid}"
Be sure to swap out your subscription GUID and Log Analytics Workspace Name along with the surrounding curly brackets.
Configure Dashboards, Notebooks, and Queries in Azure Sentinel
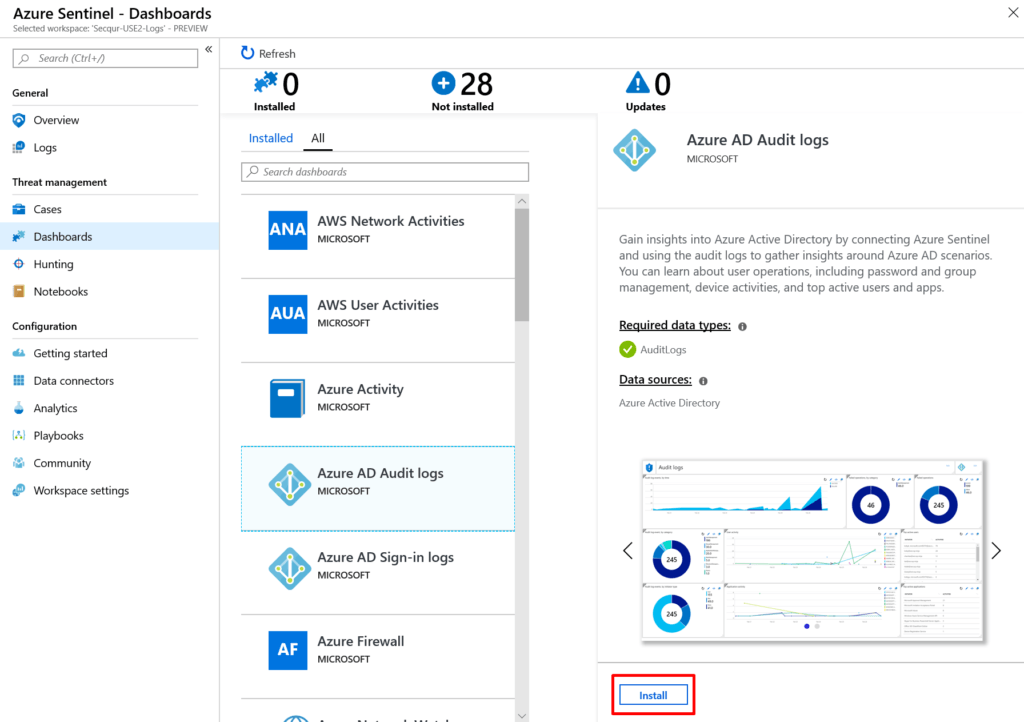
Configuring dashboards in Azure Sentinel is as easy as opening the Dashboards blade, clicking on the data connector solution that we just setup, and clicking install.
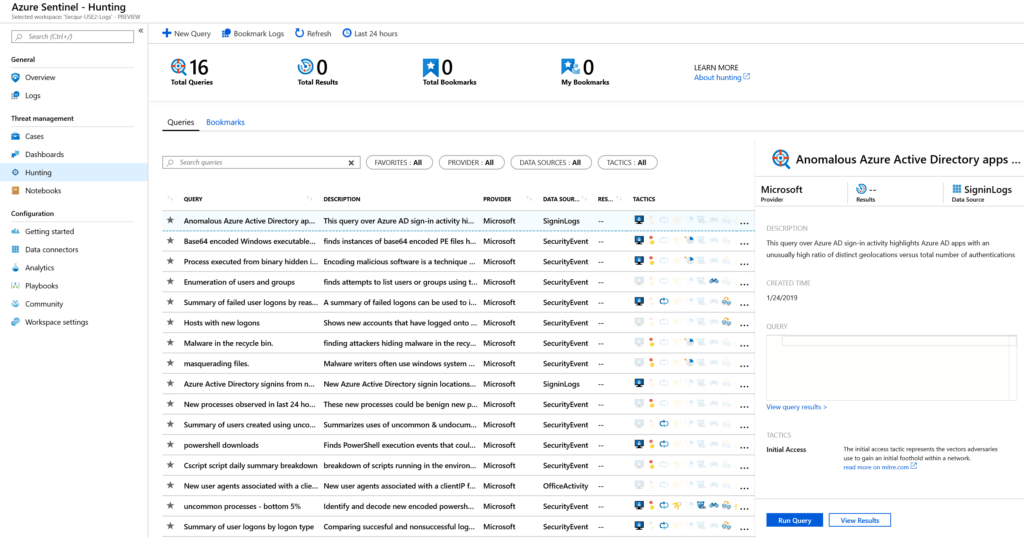
Once your dashboards are installed, you can start using them for threat hunting. Another helpful resource to identify threats is the Hunting blade, which includes a number of built-in log queries.
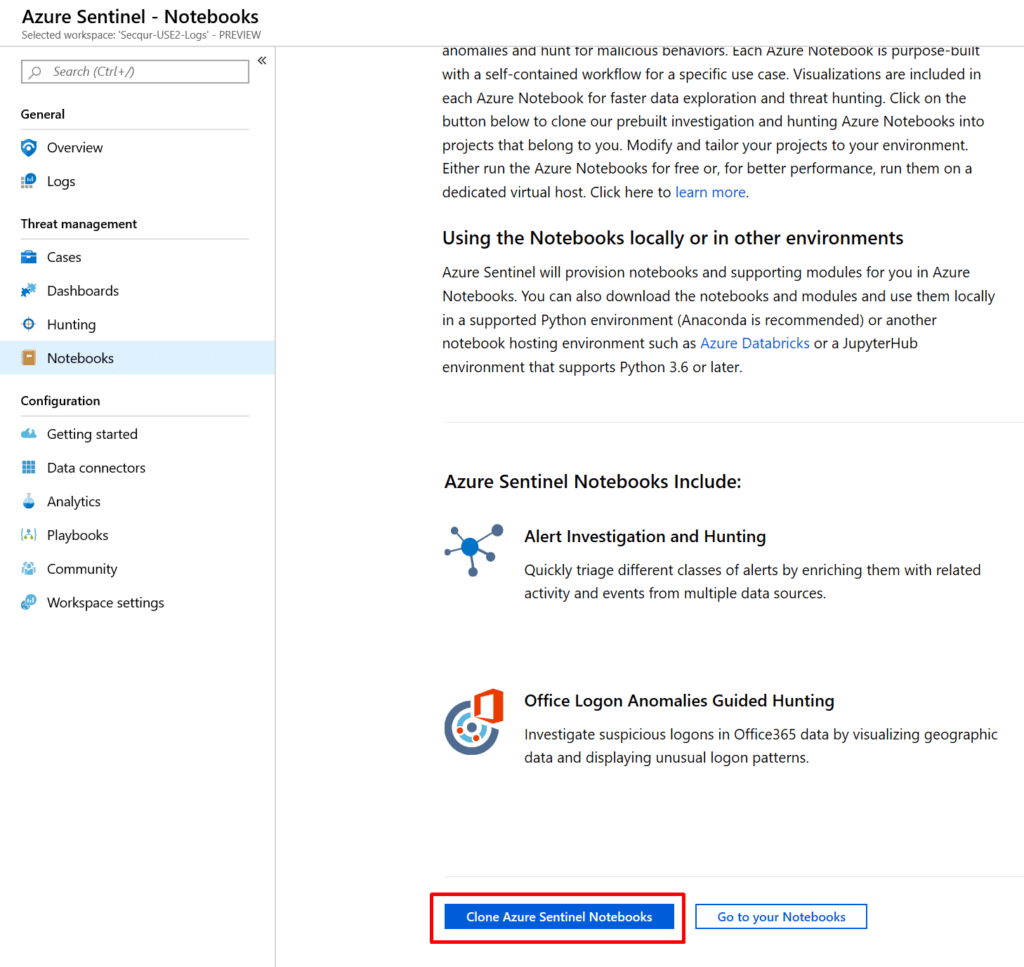
The last item that you'll want to take a look at is importing Microsoft's Azure Sentinel Notebooks from GitHub for some guided-hunting patterns. Click on the Notebooks blade and then Clone Azure Sentinel Notebooks. This will guide you through importing the notebooks from GitHub.
Closing thought on Deploying Azure Sentinel
I thought deploying Azure Security Center in 10 minutes was totally rad. But deploying a cloud-native SIEM solution in five minutes is ridiculous. Enabling Azure Sentinel is so simple, there's no reason not to do it. Unless you're the CFO and not knowing the pricing gives you anxiety. Or if you're the COO and products labeled "Public Preview" make you nervous in a production environment. Azure Sentinel is free during the public preview, and I highly recommend checking it out.
The ease of enabling telemetry from multiple data sources is mind-blowing. The innovation that Microsoft continues to make in the security space never ceases to amaze me. I am looking forward to this product going GA so we can formally incorporate it into our cloud security and orchestration platform, Secqur.
Happy hunting!
UPDATE: Azure Sentinel has been released to GA as of September 2019. Check out our Azure Sentinel pricing guide here.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
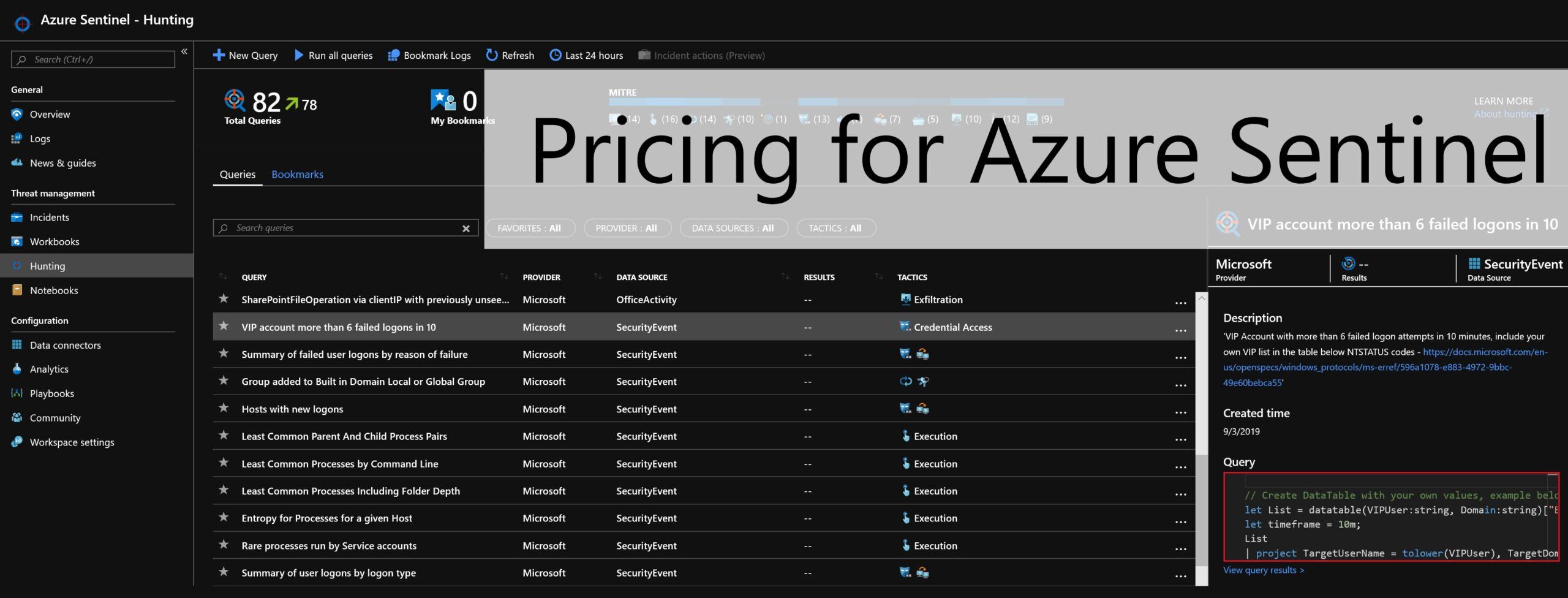
Pricing for Azure Sentinel is GA
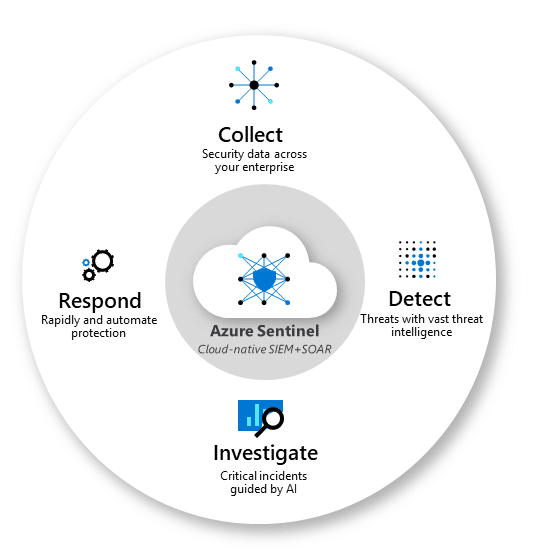
What is Azure Sentinel?

No Comments Yet
Let us know what you think