Microsoft Adds Campaign Views in Office 365 ATP Stack
Microsoft's Office 365 Advanced Threat Protection (ATP) is a robust anti-malware and virus email filtering service. With the addition of its new feature campaign views in Office 365 ATP, it just got even stronger. Now ATP can follow patterns and crafted templates to detect attacks that make use of a larger strategic plan, rather than just looking at individual isolated emails. Let's take a look at what Office 365 ATP offers and how campaign views adds to its protection.
What is the ATP stack?
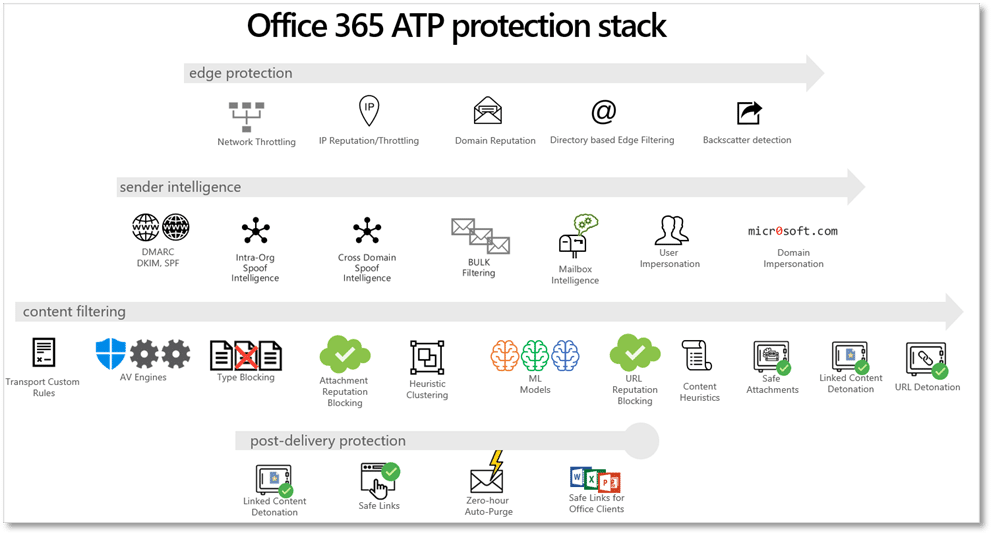
Office 365 ATP is a cloud-based service that protects against zero-day attacks and safeguards from harmful links. It also traces and reports URLs so that the administrator can gain insight into what kinds of attacks they are receiving. You can use this message filtering for your on-premises Exchange Server or SMTP environment, for cloud-hosted Exchange Online, or for a hybrid mix of both on-premises and cloud mailboxes. Here are some of the capabilities that ATP offers:
Office 365 ATP Safe Attachments
With ATP Safe Attachments, all messages are screened to look for attachments with an unknown virus/malware signature. These messages are routed to a separate environment where ATP uses machine learning and several analysis techniques to detect malicious intent. The message will only be delivered to the inbox if no suspicious activity is detected.
Office 365 ATP Safe Links
ATP Safe Links protects you from malicious URLs either in an email message or in an Office document. Any time a link is clicked on, risk is assessed dynamically. Good links can then be accessed while malicious ones are blocked.
Office 365 ATP Anti-phishing policies
This checks incoming messages for indicators of a phishing attempt. ATP makes use of multiple machine learning models which analyze the messages. Then appropriate action is taken according to the policies you've configured.
Real-time reports
Through the Office 365 Security & Compliance Center, administrators can receive real-time reports and insights about attacks. ATP will highlight and prioritize security issues, recommending ways to learn from the data and take the proper actions.
Threat Trackers
With Threat Trackers, ATP provides informative widgets and views that give authorized users helpful intelligence on cybersecurity issues.
Explorer
Also called Threat Explorer, this is a real-time report that allows authorized users to view and analyze the most recent threats. It shows data from the last seven days by default, or you can configure it to show up to the last 30 days.
Automated incident response
With the Office 365 ATP Plan 2, Automated incident response (AIR) can run automated investigation processes which respond to well known threats in existence today. Automated responses to problems are taken upon approval by your security team. With this automation, organizations can improve efficiency within their security operations teams.
Office 365 ATP for Team Sites
ATP for Sharepoint, OneDrive, and Microsoft Teams will detect and block malicious files for team sites and shared document libraries.
Attack Simulator
This is a helpful tool that will run attack scenarios which could realistically occur. There are a variety of different attack types that you can run as a drill to prepare you for what real attacks of these types might look like.
Campaign views in Office 365 ATP
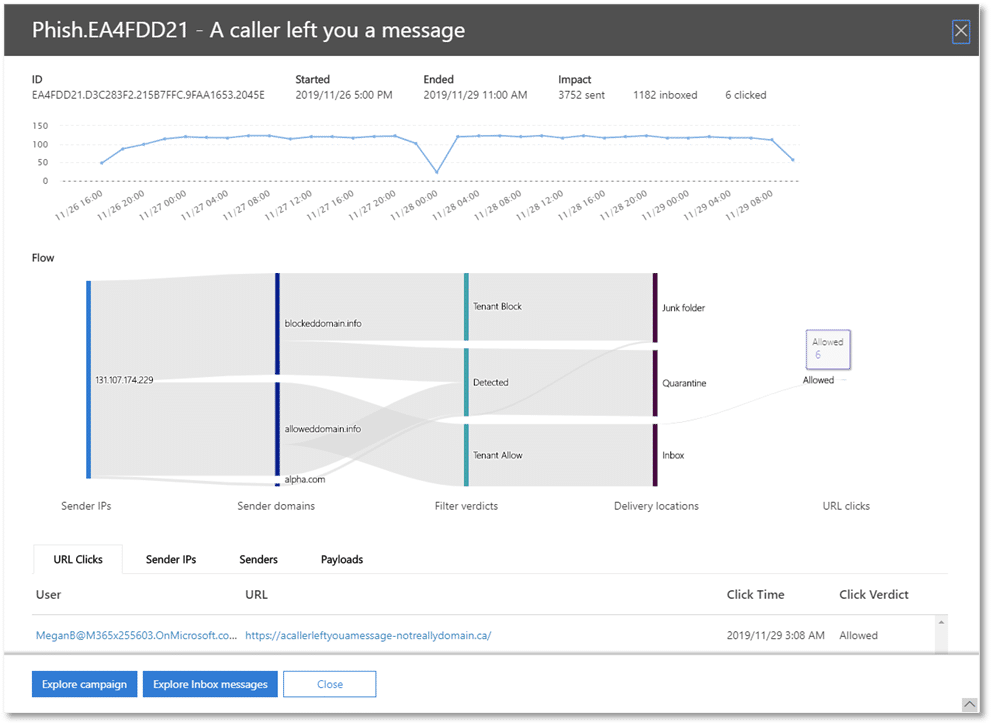
Hackers usually don't limit themselves to one email. They often use a pattern or template to craft a series of messages that come in waves. This strategic series of attacks is called a campaign (not to be confused with a political campaign, which Microsoft can also help to secure against hacking and cyber attacks---see our posts on AccountGuard and Microsoft 365 for Campaigns). A malicious campaign of email attacks is much less powerful if the recipient is able to spot these patterns with a broad view of what's going on. This is the kind of perspective that campaign views offers. It is now a section of the ATP Threat Explorer dashboard, adding a whole new insight to the previous capability of viewing only the threats in individual emails. Campaign views can identify the types of tricks the attacker is using and allow the administrator to respond quicker and more effectively.
With this new broad view, the security team can view details about the phishing campaign such as:
- The starting point and timeline of the campaign
- Its pattern and size
- How many users it affected and whether they clicked on links
- IP addresses and senders that were used to carry out the attack
- Which messages were blocked, ZAPped, sent to quarantine, or allowed into the inbox
- All URLs used in the campaign
Public preview of campaign views
This new feature is now available for public preview for customers with any of these plans:
- Office 365 Advanced Threat Protection Plan 2
- Office 365 E5
- Microsoft 365 E5,
- Microsoft 365 E5 Security
For more details about how campaign views works, see Microsoft's announcement of its preview or contact us with your questions. All of our Intelligent Threat Protection customers have the new campaign views enabled in their tenants.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Microsoft Defender For Endpoint Standalone is Now Available! (Formerly MD ATP)

What You Need to Know About Azure AD Connect V2.0

No Comments Yet
Let us know what you think