Ransomware as a Service? A Dark Web Economy for Cybercrime
We know that ransomware continues to be a big (and costly) problem to those who are targeted. Just who is carrying out these attacks, and how? Much of the ransomware activity taking place today does so through an interconnected network of actors working in a gig-like economy. Malicious actors with little more than a laptop can now make use of resources available in Ransomware as a Service offerings. Unfortunately, that makes it all too easy for cybercriminals to get involved and launch these attacks.
Ransomware as a Service (RaaS!)
Almost as a mockery to legitimate technology service offerings such as Software as a Service (SaaS), experienced cybercriminals are renting or selling their tools in a Ransomware as a Service model. They offer the ability to purchase access to their payment infrastructure, data leakage and ransomware payloads. Conti, REvil, and Hive are examples of these RaaS programs.
RaaS kits can include bundled offers, customer service support, forums, and/or other features. Some programs have a fixed price for a RaaS kit, while others take a percentage of the profits made in successful attacks.
Sometimes templates are offered to guide actors through standard attack processes: initial exploitation of a vulnerability or access via malware infection; credential theft; elevated privileges; and lateral movement throughout a network. By this point large amounts of data, and access to the network itself, can be held for ransom until the victim is forced to pay and those involved in the attack process reap the payload.
A Specialized Economy
These underground connections facilitate ransomware attacks, making it easier to carry them out---which isn't good news for their targets. The dark economy of ransomware gets broken down into specialized roles. For example, an access broker sells access to networks already compromised. A RaaS operator develops and maintains the tools that the service offers. Down the line, a RaaS program may have over 50 “affiliates” using the service, leveraging and contributing various tools, skillsets, and objectives. Thus, when one company is compromised in an attack, there are generally various actors behind it who contributed at different stages. Smaller attacks are connected to larger ones, such as the malware that steals passwords and then uses that information to lead to bigger devastations.
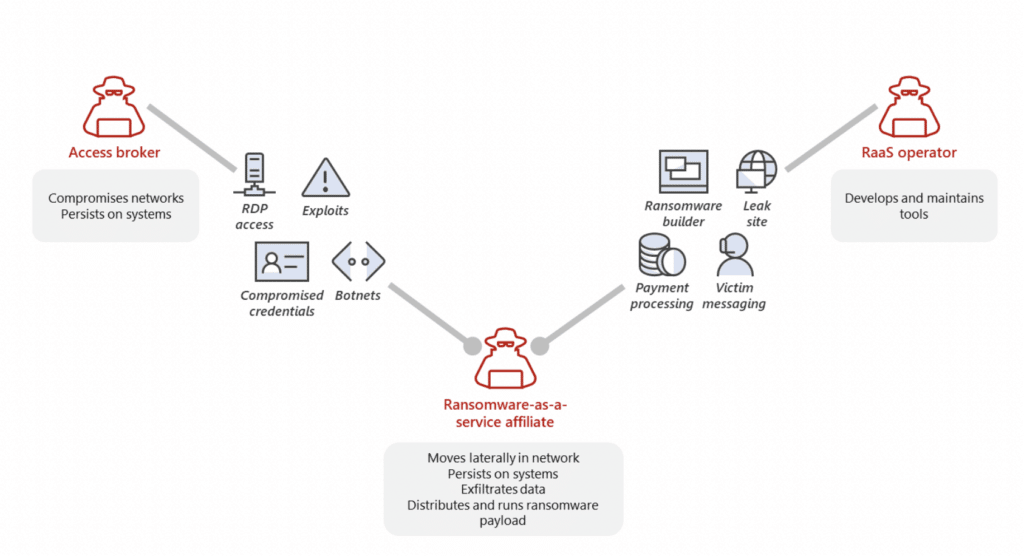
In this RaaS economy there's room, and a relatively easy path, for newcomers without much experience or sophistication. Newer criminals willing to pay for the service or contribute a share of their earnings become an additional income source for the operators who create the programs and offer the services. Then both benefit from the gouging of victims that they collectively take part in. (I can't help drawing some similarities to pyramid schemes---but the affiliates in ransomware programs come out a lot richer.)
This specialized economy has changed the way ransomware attacks are done. Earlier ransomware methods targeted broadly, casting a wide net in order to catch a few. Today's ransomware criminals vary their attack patterns depending on their discoveries of vulnerabilities, which may be made by specialized actors in the course of the process. This active human involvement leads to more finely targeted attacks with a higher success rate.
Movement Between RaaS Programs
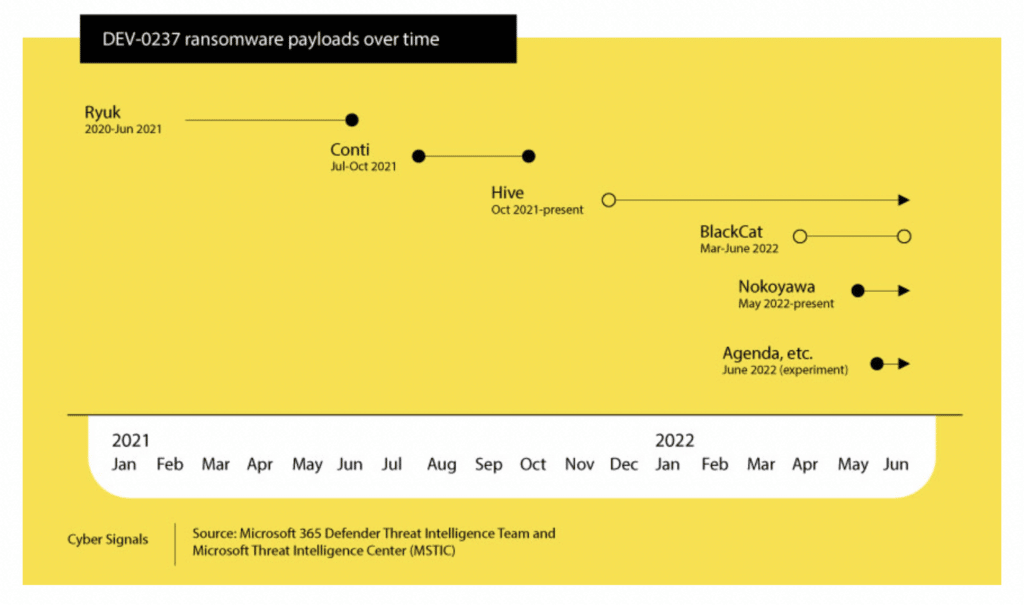
Sometimes these Ransomware as a Service programs break up and dissolve, and new ones emerge in their place. (In the yellow chart above, you can see that Ryuk, Conti, and BlackCat have ceased, while others that have come about are still currently in service.) Affiliates that had been using services that shut down move on to others, and may break up their work between multiple programs. This movement between payload programs obscures who is involved in which of them, making it difficult and confusing for law enforcement, governments, and security defenders trying to track these malicious actors.
Defending Attacks Generated by Ransomware as a Service
One of those security defenders tracking ransomware activities is Microsoft. As any organization can become a target for this increasingly sophisticated underground economy, Microsoft recommends preventative actions such as improving credential hygiene, auditing credential exposure, and reducing the attack surface. For more details, see this article on common security weaknesses and actions to build better defenses.

More on ransomware and cybercrime:
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts

Microsoft Compliance Manager Now Available for GCC & GCC High

Great Customer Relationships Means Great Communication

No Comments Yet
Let us know what you think