There’s a misconception out there that ransomware is declining and becoming a threat of the past. This assumption can be dangerous, though, because it’s not accurate—as our own interns have learned. Ransomware attacks did decline over the course of 2018, but that lull didn’t end up being a continuous trend. Increased ransomware attacks and their severity in 2019 suggest that we should be more concerned than ever. Coveware’s report from quarter 4 of 2019 shows that the average ransomware payment more than doubled that in quarter 3. McAfee says that it has increased 56% over the past four quarters, and Comparitech predicts that this problem will continue to increase at “an incredible pace.” RSA Security also predicts that future ransomware attacks will disable account access in addition to data and files. It looks like ransomware is now cybercriminals’ most preferred method, and it’s not going away anytime soon.
How ransomware works
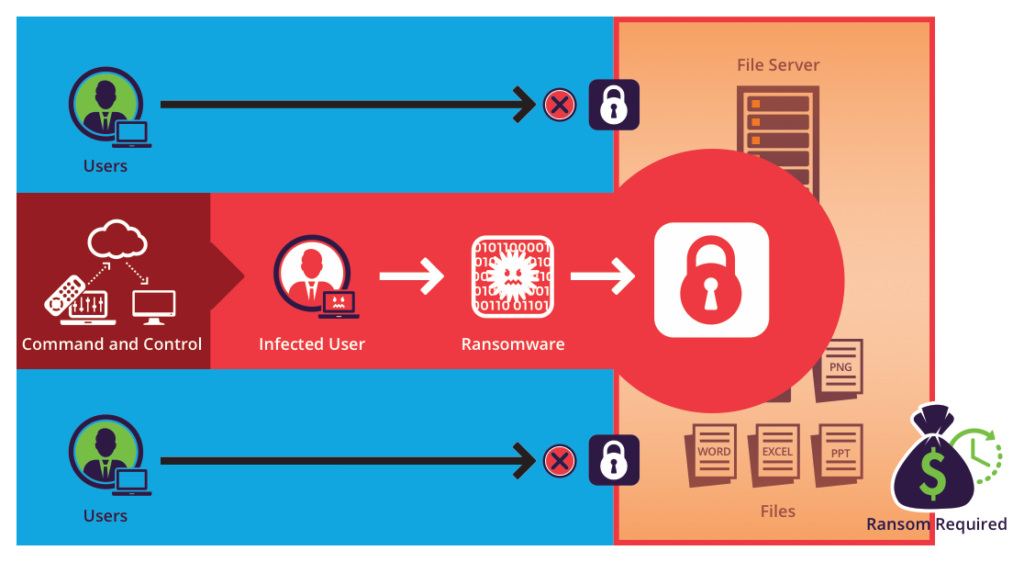
As with pre-cyber traditional ransom, a perpetrator holds stolen valuables hostage until a payment is made to retrieve them. Hackers can take over data, a website, or an entire computer system and demand payment to get access back. They encrypt the data or system, allowing decryption only with the ransom payment (which, by the way, is just about always transacted in Bitcoin). This payment can be a nominal amount across a wide group of people or a very large sum from a big corporation, government agency, or even a city. (Hackers demanded $76,000 in Bitcoin when they attacked Baltimore last year. The city refused to pay it and was able to fix its own computer systems–but that took a lot of time, inconvenience, and a much higher net cost in the end.)
The evolution of ransomware
Originally, ransomware’s goal was quantity. Attackers targeted large numbers of computers through spam emails and malicious URLs that hosted exploit kits. But cybercriminals have increasingly taken a different approach more recently. In 2019, many attackers seem to have been more interested in finding good, high-value targets and spreading laterally through those networks rather than over the internet. Once penetrated into one of these high-value systems, the attacker then aims to hit as many endpoints as possible to make that victim’s attack devastating. Then, the perpetrator demands a higher ransom than in the broader attacks of the past. Coveware puts the average payment in quarter 4 of 2019 at $84,116–with ransoms as high as $780,000 (in the Ryuk ransomware variant). And that’s not even considering downtime, which also costs a company a lot in decreased productivity. Average ransomware downtime has also gone up, from 12.1 days in quarter 3 to 16.2 days in quarter 4. So, ransomware is becoming more costly, more time-consuming, and more devastating.
Now ransomware criminals have formed a sort of underground economy, offering Ransomware as a Service and making it easier for inexperienced criminals to get involved by purchasing access to tools. Read more about that here.
Ransomware is still a problem and how to protect against it
While ransomware is still a problem with growing consequences, the capability of enterprises to protect against it is also increasing. So, the good news is that we have tools to ramp up your security and keep ransomware attackers at bay. Here are some recommendations to protect yourself:
- Keep up with patches and updates. It should go without saying that you keep your enterprise on top of this. It’s relatively easy maintenance that can save you a lot of trouble.
- Educate users about risk, prevention and policy. Make sure IT administrators have a firm understanding about your company’s security policies and practices, and train other staff to be on the lookout for suspicious emails. Training sessions dedicated specifically to cybersecurity are a good idea.
- Restrict access where possible. If fewer users have access to valuable data, then fewer accounts can be affected. Categorize users according to their access levels and grant only enough privilege for users to do the tasks their jobs require.
- Use biometrics and/or multi-factor authentication. This can help protect your company from RDP brute force attacks.
- Consider a bastion host. This is a specialized node that processes and filters all incoming traffic, acting as a gateway and preventing malicious traffic from entering the network. Since it’s deliberately exposed, it needs to be streamlined, removed of any unnecessary software, and strictly monitored and maintained. But it can help guard the network behind it, and in some cases it can even draw attacks in order to deflect them and trace their source.
- Monitor continually with good anti-ransomware guards. When it comes to cybersecurity, Microsoft has got your back–and we do too. A security plan costs a lot less than a ransomware payment.
- Look into file integrity monitoring (FIM). This security technique measures any aberrant activity against a normal baseline that you set. It can keep a constant eye on any changes that occur and alert you accordingly.
- See more of Microsoft’s tips on defending from ransomware.
- Contact us for strategic advisory on how to equip yourself with the best protection. You can also read our Guide to Ransomware Protection with Microsoft 365. As one the top 10 security providers, we’re here to help you keep your company safe.

