A Zero Trust Guide for Azure AD
In today's digital world---especially with the additional remote work taking place under shelter-at-home practices---it's crucial to have a strong security framework. We've discussed before how a Zero Trust policy provides solid protection against attacks. But implementing this practice does take extra work. Let's go over some guidelines that can help get you started with this vigilant security model by looking at its core principles and how they would play out within a Microsoft Azure Active Directory (AD) service, using Azure AD Connect if necessary. Here's a Zero Trust guide for Azure AD.
Three Principles of Zero Trust
The Zero Trust model assumes that every entity is a potential risk, both outside and inside a network. Operating under this framework means setting up strict security measures and adopting principles that will keep the tightest reign on possible breaches:
- The principle of least privilege. This means granting file or account access only to those who need it, when they need it. It gives each employee the least amount of privilege they need to do their job.
- Explicit verification. Zero Trust demands verifying user credentials at all times, through the strongest methods.
- Assumption of breach. Rather than assuming certain areas are safe, the Zero Trust model works on the basis that breach can and will happen anywhere.

Zero Trust within Azure AD
To set up a Zero Trust model within Azure AD, you'd want to make every access request go through Active Directory. This means connecting every user, app, and device to it, and using Azure AD as your identity control hub. This centralizes and strengthens your security foundation. Once you have everything integrated, you can automate the way your user identities are provisioned into your applications, and begin to analyze logs that tell you about how these connections are operating. Then, you can take specific measures to line up your security with the Zero Trust principles:
Create an Environment of Least Privilege
These are ways you can use Azure AD to regulate user access so that it's only applied when necessary:
- Conditional Access. Set up both active and fallback policies in your deployment. You'll need to configure your IP locations according to risk.
- Privileged Identity Management. Identify which of your users play a privileged role, such as administrators of different areas. Then remove the specific accounts of those who don't need them, and categorize them according to their level of access need. To make this easier, Microsoft has a 12-step guide for implementing Zero Trust identity management in Azure.
- Consent to Applications. Manage consent requests to restrict users from allowing applications access to your company data.
- Entitlement Management. Since your apps will be centrally authenticated through Azure AD, you'll be able to keep a streamlined trail of which users have access to what, and why they have it. Users can request "access packages" that you set up, for example when they need access to files for a project. (This feature is only available through Azure AD Premium P2.)
Verify Users at All Times
- Azure multi-factor authentication (MFA). Strong verification is possible even as your users change devices and locations, with multiple factors required for access. You can make this mandatory by blocking legacy authentication.
- Azure AD Join (or Hybrid Join). This allows you to manage client access to data depending on whether the user's machine is one that your organization can control.
- Microsoft Intune. Enabling Intune gives you greater control over your users' devices. Details about the devices they're using, such as whether they're jailbroken and how well they're patched, will inform the amount of trust you assign them.
- Passwordless authentication. Azure AD supports FIDO 2.0, so you can make use of it in implementing the strongest form of verification: biometric credentialing with no passwords involved.
Take Precautions that Assume Breach
- Azure AD Password Protection. In the meantime if you haven't gotten biometrics running yet, be sure to use Password Protection to strengthen the passwords your users can create. Many passwords are easily attacked, even under classic complex password policies.
- Identity Protection. Available within Azure AD Premium 2, this tool allows you to detect and investigate identity-based risks.
- Restricted Sessions. When users are low-risk but their current devices aren't, you might make use of restricted sessions. For example, the user can read messages or view data, but cannot download it to that device.
- Integrations with Microsoft Cloud App Security (MCAS). Enable MCAS integrations with Conditional Access, Identity Protection, and Azure Advanced Threat Protection (ATP). This brings greater awareness to Azure AD, which then allows for better responses to potential threats.
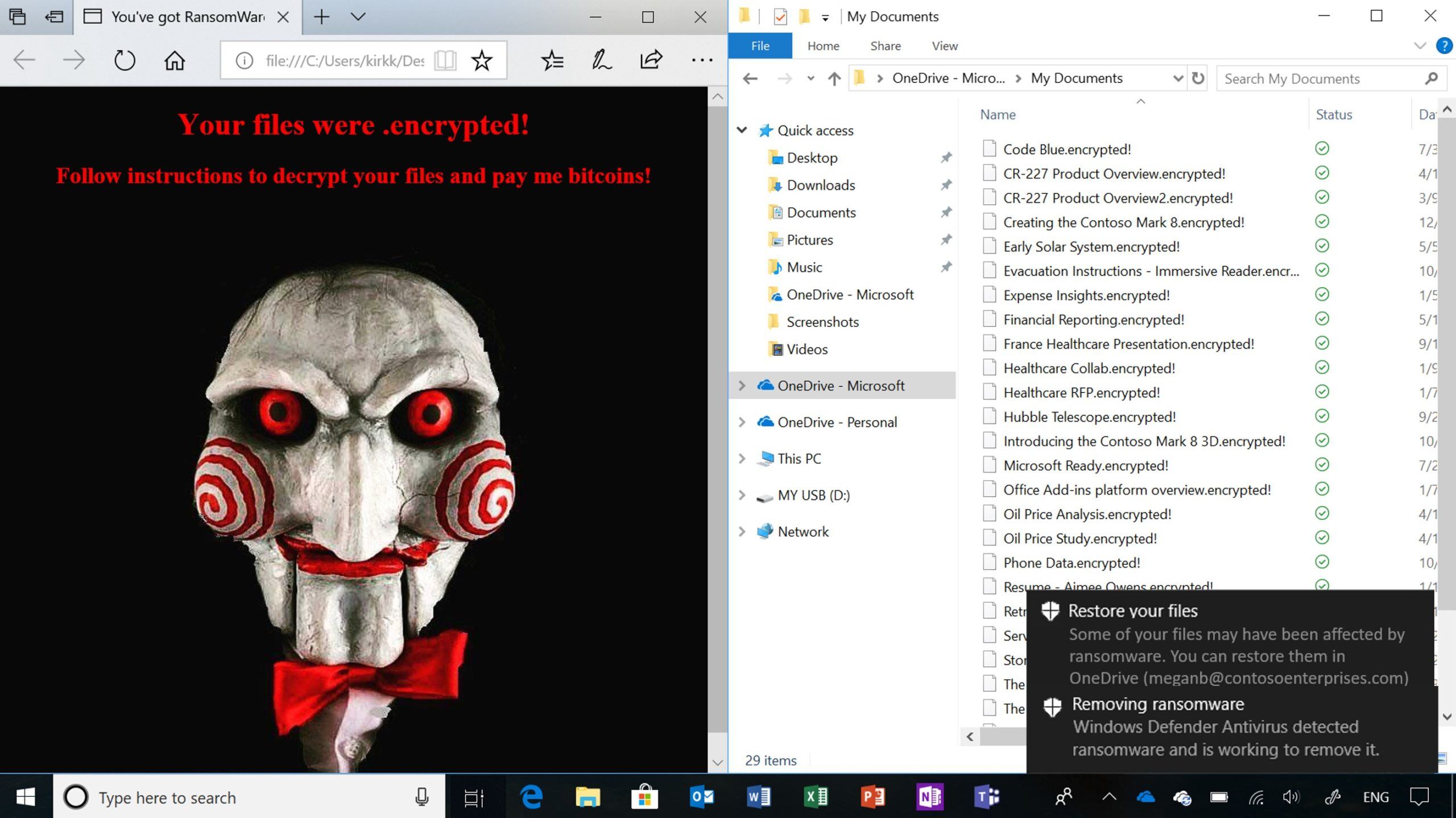
- Enable Microsoft Defender ATP. This gives you the ability to react to a malware attack at near real time. It detects patterns among multiple user devices and responds to untrustworthy actions by raising their device risk (or user risk) immediately.
Conclusions On Our Zero Trust Guide for Azure AD
With so many tools and capabilities, Azure AD sets the scene for a rock-solid, Zero Trust security foundation within your organization. We understand that it also presents a lot to think about and configure, so we're happy to help---security's kind of our thing. Let us know if you have questions or need more guidance, and we'll make it happen.
For more on the general concept of Zero Trust, check out this interview with its creator John Kindervag.

Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Top 10 Security Best Practices with Microsoft 365 in 2021

Gartner's Unified Endpoint Management Leaders

No Comments Yet
Let us know what you think