A Guide to Ransomware Protection with Microsoft 365
Protecting modern IT systems from ransomware is fairly simple now with Microsoft 365. Microsoft uses AI models and machine learning to process 6.5 trillion daily signals with a team of 3,500+ full-time security engineers that invest $1 billion annually in R&D. To put that in perspective, a managed SOC like Arctic Wolf processes "only" 20 billion signals a month. Excluding Symantec and McAfee (with their 10,000+ person sales teams), companies like Arctic Wolf, Darktrace, Carbon Black (just acquired by VMware), and many other security firms have fewer than 1,000 total employees with less than $1 billion in revenue. It's not even close.
What we typically see is one of two scenarios in most organizations which lead to being exposed to ransomware attacks:
- Investing too little: A reluctance to invest in modernizing their IT systems. Whether it's fear of change, cost concerns, or something else.
- Investing too much: Too many security vendors that don’t integrate with each other, which creates too much complexity to manage quickly and efficiently.
The hard truth is that a firewall with IDS/IPS and antivirus on your desktops can’t stop modern attacks. Modern cybersecurity involves a defense-in-depth process that looks like the following diagram when you standardize on the Microsoft 365 platform:
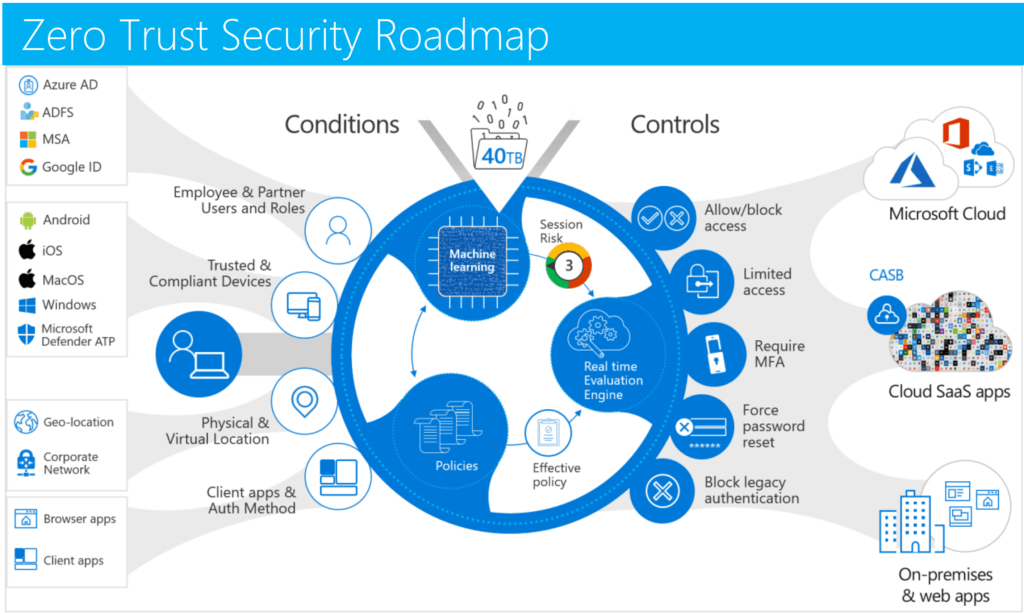
Key focus areas for Ransomware Protection with Microsoft 365
1) Microsoft Intune and Conditional Access for MFA
- MFA is the number one way to protect a user’s identity. 99% of identity breaches can be blocked with MFA.
- Conditional Access with Intune allows you to only challenge for MFA sign-ins if the account is breached or outside of your allowed parameters.
- Intune can also be used to rapidly deploy Windows 10, including drivers, applications, custom configurations, and active directory domain join the device using a feature called Windows AutoPilot Self-Deploying mode.
- Microsoft Intune protects organization data on both personal and corporate mobile devices using MDM / MAM policies.
- Intune can configure OneDrive Known Folder Protection on a device anywhere in the world without requiring a VPN connection to your LAN, and allows you to recover from a ransomware attack on workstations within about an hour.
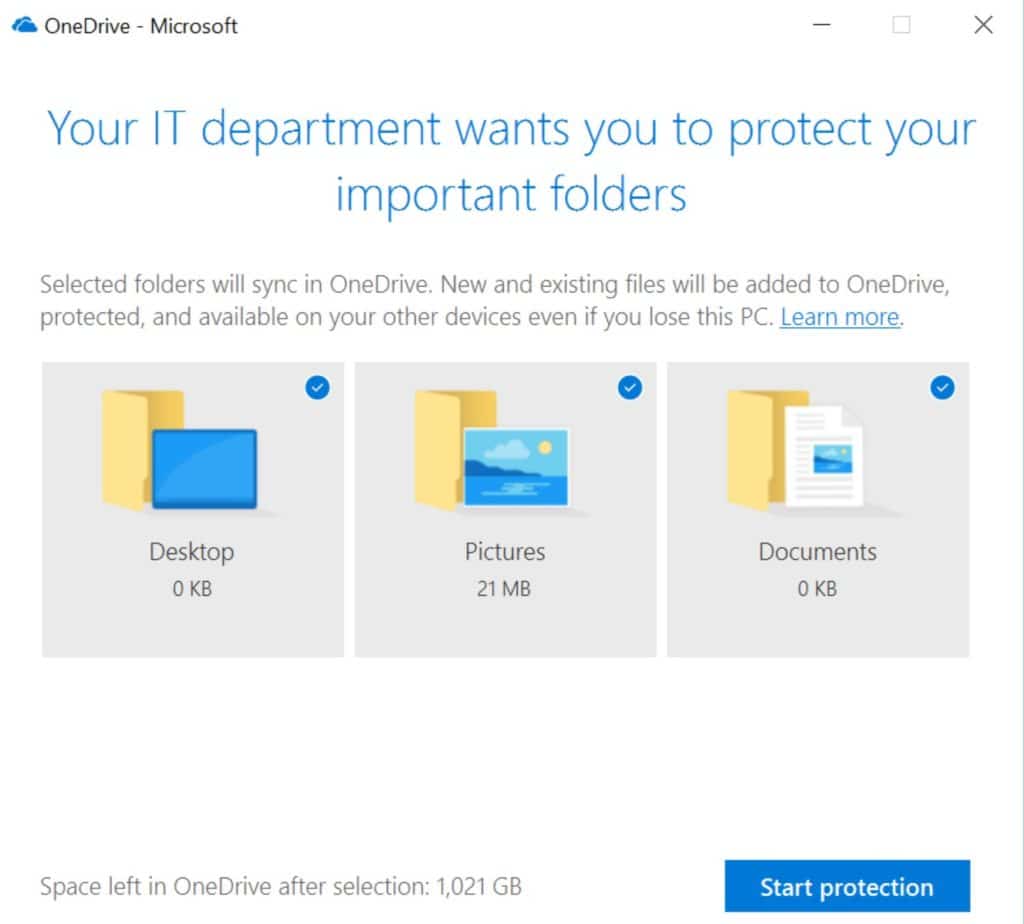
2) Offsite Backups
- OneDrive Known Folder Protection automatically backs up workstation’s desktop & documents folders and keeps 1,000 revisions of files in Microsoft's cloud.
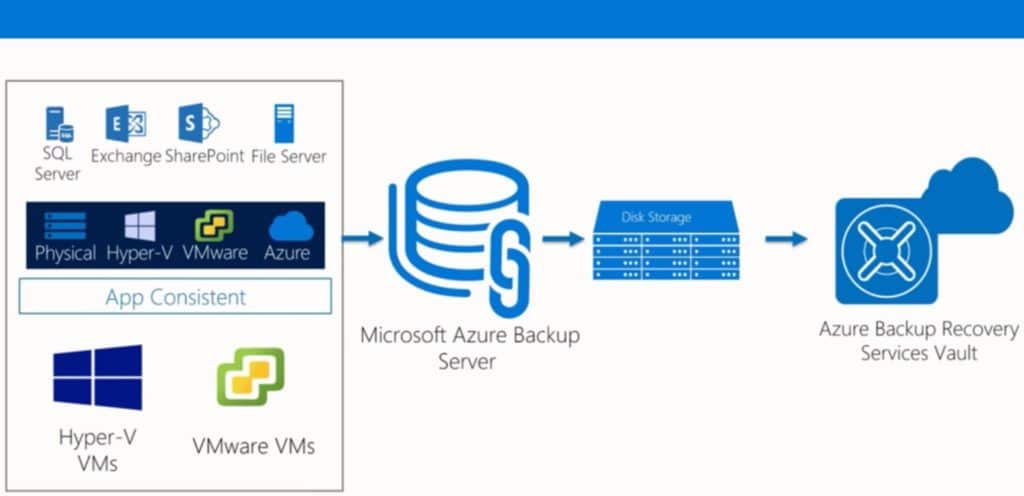
2. Azure Site Recovery, Azure Backup, and Microsoft Azure Backup Server (which is basically System Center DPM without the Tape module) ensure that you have off-site backups for recovery of files that are affected. With recently announced price reductions of up to 50% for Azure Archive storage, these options are even more viable today.
3) Next-generation Antivirus with Microsoft Defender ATP
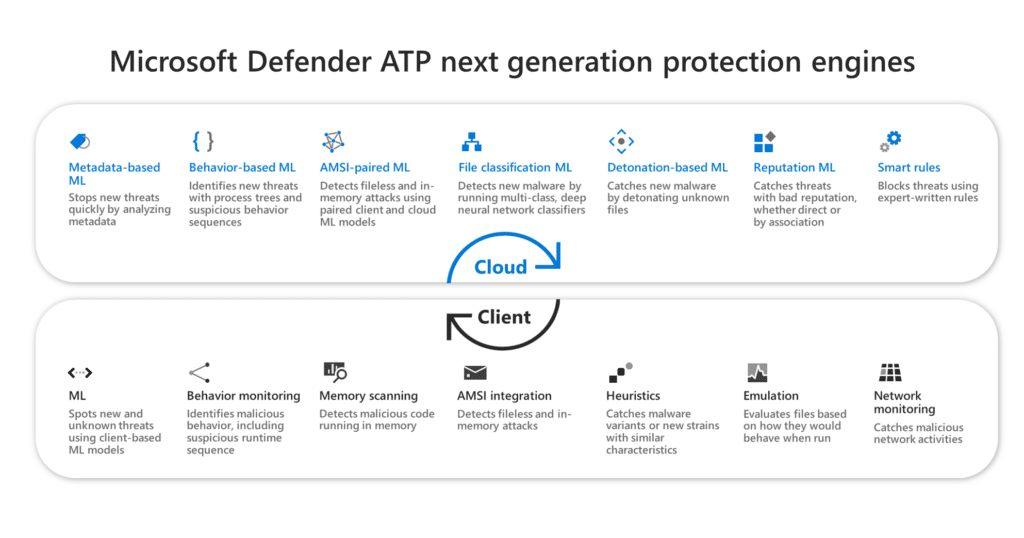
Microsoft Defender ATP, a part of Microsoft 365 E5 Security, will protect against all known ransomware variants and automatically isolate infected machines. Some additional features of Microsoft Defender ATP (formerly Windows Defender ATP) include:
- Compatible with Windows 7 and newer on the client, and Server 2008 R2 or newer on the server, as well as MacOS.
- Kernel level tracing to block supply chain attacks from backdoors in hardware drivers.
- Secure boot to block rootkits.
- Protection from file-less attacks that never write to disk and only live in memory.
- Protection from mimikatz-like password theft attacks.
- Controlled folder access to block ransomware.
- Device-risk profiles based on anomalous behavior that can be used to block access to Office 365.
4) End-user Training and Protection
- Simulating phishing attacks to train users and performing routine password spray attacks on your users.
- Using Office Advanced Threat Protection (ATP) to block malicious email URLs and attachments at the time they click the link.
Items 2.1, 3, and 4.2 can be implemented with zero noticeable impact on your users. Yet these few changes can reduce your risk of suffering a breach by 40% and a crippling ransomware attack by up to 95% on workstations.
At Infused Innovations, we typically deploy everything above in a series of the Zero Trust Accelerators that target:
- Deploying tools for modern authentication and an identity-based security perimeter.
- Managing devices anywhere in the world, and encrypting the data on those devices. Both personal or corporate-owned.
- Enabling Microsoft's cross-platform threat intelligence tools for automated and orchestrated security responses.
The Zero Trust Security Accelerators complement our security management services that cover everything from user training, to performing compliance controls, ensuring patch management, and active threat hunting. For more information, download an overview of our Secqur Aether service to create your Secure Intelligent Workplace.
Can your current antivirus block an infected device from encrypting data on network shares or in cloud document libraries?
Pro tip: Microsoft Defender ATP can.
Am I Doing Enough to Protect Against Ransomware Attacks? Should I switch to Microsoft 365?
Some prospects we run into think they have a comprehensive cybersecurity plan in place. Some of them do, but one way to tell is if you can answer simple questions like:
- What was the extent of your last breach? If your answer is that you haven’t been breached, we're willing to give a free cyberattack assessment to prove otherwise.
- How long does it take you to identify and respond to a breach?
- What is your breach response policy to notify customers that you have suffered a breach?
- What reports can you run in the next 15 minutes to prove you’re not currently breached?
- How do you monitor your current attack and risk surface? Has there been an increase in attacks for a given threat vector in the past week?
- If a file-less attack gets past your firewall, what tools do you have in place to identify unusual behavior?
- How do you prevent users from downloading work data on personal devices?
Our CISO has expressed his thoughts, that if you're not on Microsoft 365 (or at least EM+S) then you're leaving your organization open to attack.
But I Have Cybersecurity Insurance for my Ransomware Protection!
And it goes without saying that if you answer "well I have a cybersecurity insurance policy" to any of those, it's an immediate failing grade. Not that there's anything wrong with having insurance, but having insurance isn't a replacement for a smart strategy (and without a smart strategy, your insurance policy won't pay out anyway).
If you’re not using a zero-trust framework with a defense-in-depth approach, then you have no way of rapidly identifying and limiting the impact of breaches when they happen.
Centralized Monitoring with Azure Sentinel and Azure Security Center
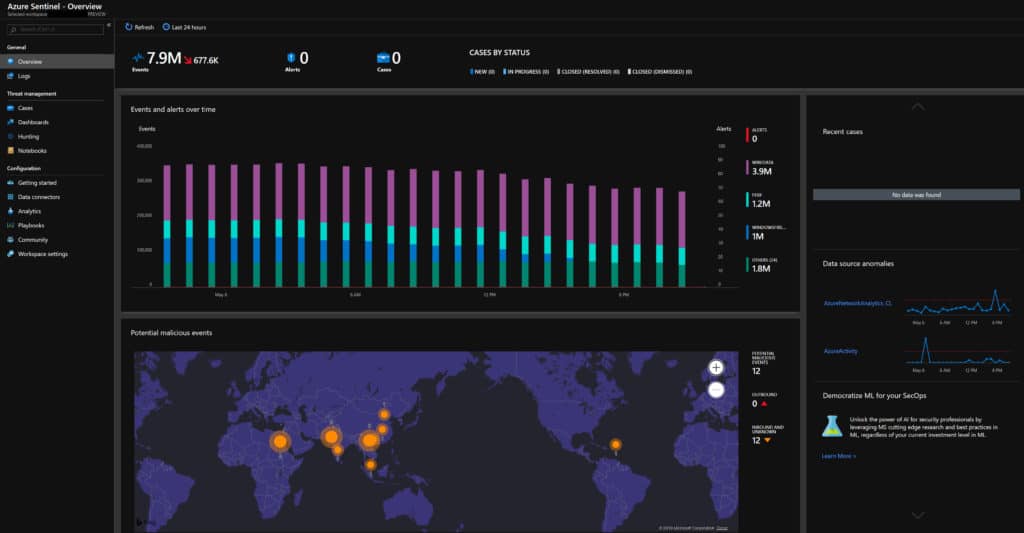
Even many of our smaller clients are implementing comprehensive SIEM / ATP / CVE solutions on their servers via our managed Azure Sentinel and Azure Security Center services to satisfy cybersecurity requirements for insurance policies across their on-prem and cloud environments. Even a simple breach that results in a spear-phishing attack where an attacker impersonates your domain to intercept wire payments can easily cause $75k in lost revenue. And if your organization is the source of the breach, your insurance doesn’t have to pay if they can prove negligence.
Besides the deep integration of their 90+ cybersecurity solutions, Microsoft’s suite of tools is reasonably priced in comparison to other vendors. Other SIEM solutions also don't include ATP or CVE scanning (which comes with Azure Security Center licensing) and start at:
- $10,000 - 20,000/yr for Splunk (Yes, there is a free community edition to play with)
- $43,000/yr for LogRhythm for a single server
- $65,000/yr for QRadar
- Versus $200/yr per server for Azure Security Center... with no minimum startup investment like the other solutions
Some basic security hygiene principals don’t require fancy paid security tools either:
- Don’t allow desktop accounts with email enabled to have administrator privileges
- No shared accounts - use named account only; for kiosk accounts, consider using a FIDO key with Windows Hello; use group managed service accounts for automatic password rotation on service accounts
- Patching all your devices within 30 days of a release, including third-party software
- Chocolatey is a free open source software package management platform that uses NuGet to easily manage your third-party patching
- Limiting automated external mail forwarding at the organization level
- Configure DMARC, DKIM, and SPF records in your public DNS
- End-user training for phishing attacks
Closing Thoughts on Ransomware Protection with Microsoft 365
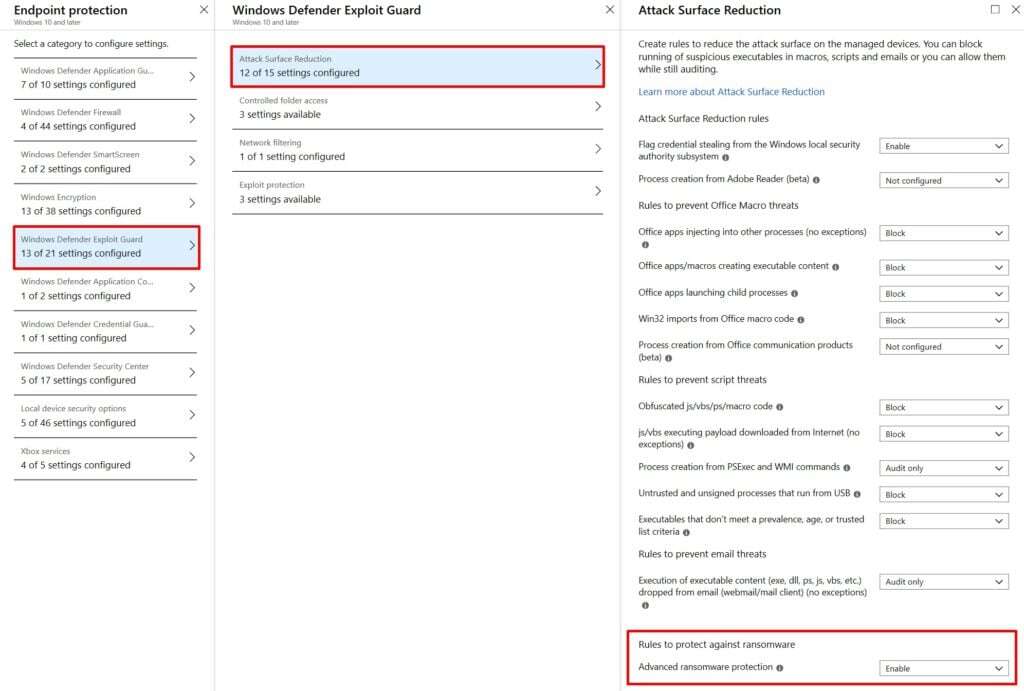
The main take-away from all this should be that antivirus and IDS on your firewall aren’t enough to block modern cyberattacks for on-prem or hybrid infrastructure. It is possible to prevent ransomware attacks using modern cybersecurity solutions. The screenshot above shows how easy it is to enable advanced ransomware protection using the Exploit Guard and Attack Surface Reduction policies in Intune. On top of the potential loss of productivity, new legislation is requiring organizations to either take a proactive approach to secure sensitive data or face steep fines and potential jail time. If you have compliance requirements, then complacency is not an option.
We’ve architected solutions for SCADA, GDPR, CCPA, HIPAA, PCI, FedRAMP, and CJIS environments. (And a few more acronyms, I'm sure.) We built and secured the cloud infrastructure for a large New England DOT (Department of Transportation) crash database system on Azure. I'm personally volunteering 1:1 time with our CISO, Dan Chemistruck, if you would like to discuss any compliance requirements or governance questions about modern security practices. Just submit the contact form below to schedule a call.
One of our key mission statements at Infused Innovations is to help make the internet a safer place.
Infused Innovations is here to help and we have a number of proof of concepts and demos showing the breadth of security services that we can provide. We have no shortage of walk-throughs for various attack vectors and how to automate responses to them. Many of these demos are geared towards creating the motivation needed from the executive suite to understand why investing in cybersecurity is not just important, but required in modern IT.
If you are interested in Windows Autopilot for Workstation Imaging, you can read up on it here.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Budgeting for Microsoft Defender XDR and Zero Trust Security

The Complete Office 365 and Microsoft 365 Licensing Comparison

No Comments Yet
Let us know what you think