Zero Trust Security Concepts and Microsoft 365
88 records were lost or stolen every second in 2017, and that number is only likely to increase. The two most common settings for these breaches to take place are healthcare and banking as a distant second. As companies move to ensure their entire supply-chain is compliant to meet strict regulations, such as GDPR and CCPA, this situation means that the stakes are higher than ever for companies to try and show to customers and regulatory bodies that they are taking the necessary steps to ensure that their data is secure. Fortunately, one of the major innovations from every major security vendor is zero trust security concepts.
The basic premise of Zero Trust Security concepts is getting rid of the paradigm that data is secure as long as it is within the corporate network. Instead, there are new measures to make sure that data is always secure, and access is only given after meeting a set of conditions. Granting blind trust is no longer automatic for your corporate LAN or corporate devices.
This may sound overly complex, but Microsoft 365 simplifies this by supporting Zero Trust Security out-of-the-box. This insight can make a complex process on paper become a lot easier to deploy.
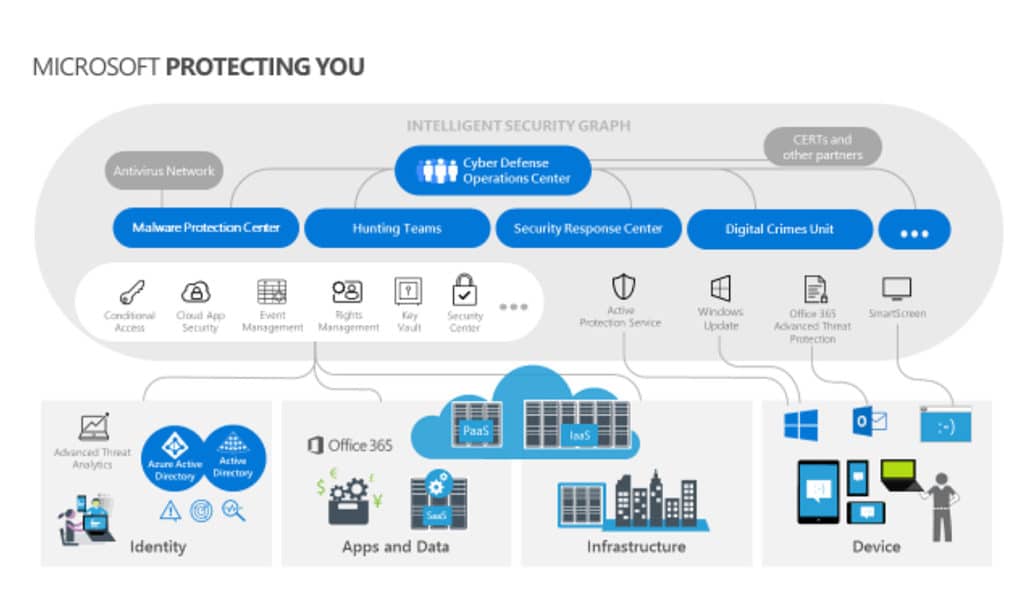
The Microsoft Intelligent Security Graph
The fundamental starting point when it comes to creating a zero trust system through Microsoft 365 is the Microsoft Intelligent Security Graph (MISG). All 365 services write to the MISG, allowing every service that you use to write separate user/device risk profiles. This is a major boost for your Governance, Risk, and Compliance efforts. The MISG bases its threat detection off of trillions of different signals collected daily.
Perhaps one of the best examples of this information being put into action is through Conditional Access. CA is a feature available in Azure Active Directory versions Premium 1 and higher. In the past, one of the first lines of defense for information security was a firewall. However, the functions of a traditional firewall no longer align with the way we use technology. Employees are accessing your data and resources through a variety of different devices and apps, and firewalls are no longer effective when the employee is outside of the office. The good news is that conditional access makes this problem easier and more efficient to tackle.
How is this the case? Conditional access gets around this problem by providing a set of dynamic access control decisions for every resource request. These are based off of the user, device, location, and session risk, and differ every single time. Data from the MISG determines whether or not a session is risky. Conditional Access then provides access based on the risk profile rather than an easily stolen password.
For example, if a CEO was to access their email from an unusual country, conditional access would note that something is off, and can require that the device accessing the data must be Azure AD registered, compliant with Intune-defined security policies, and up-to-date with basic security hygiene standards. However, if the user profile is at a high risk, you can dynamically require an MFA challenge as well. Otherwise, the request will be denied. As a result, your CEO can work seamlessly while they are on their honeymoon, as long as they are using a compliant device.
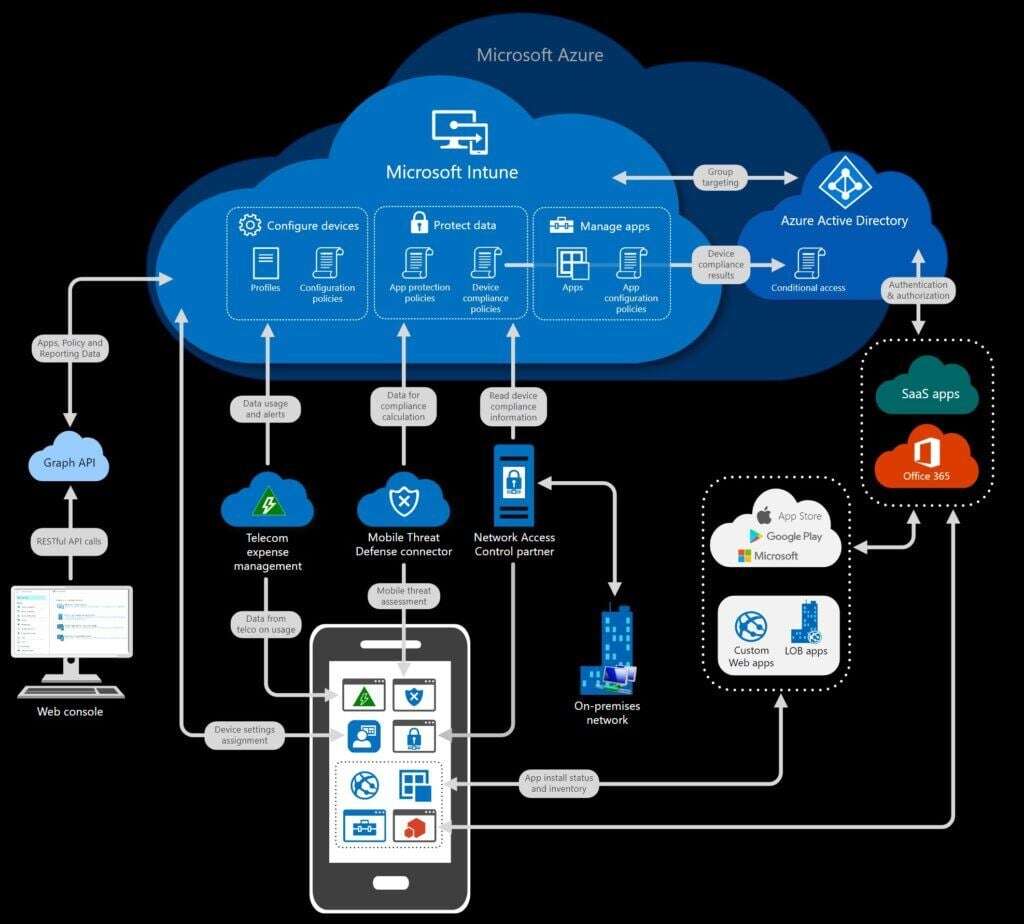
Zero Trust Security Concepts with Intune
Intune is another branch of Microsoft 365’s zero trust security measures, focusing on mobile devices, apps, and PCs used in your organization. The main purpose of Intune is to register any device or application that your company and staff are using, whether it’s Outlook or Nine running on a company mobile device, laptop, or personal device that the employees bring themselves to use for work. This saves effort for your IT and security teams alike.
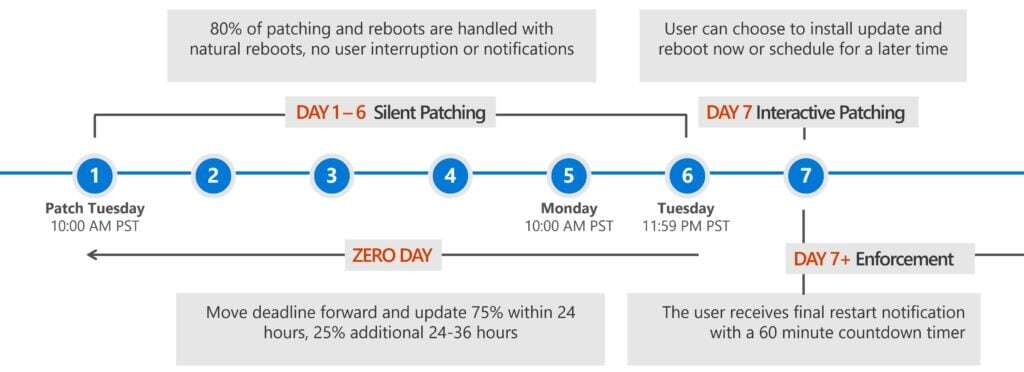
When the devices are registered, Intune will determine whether or not each device that accesses company resources is compliant, based on the standards you create, as well as an inherent machine risk level provided by Microsoft Defender ATP (more on that in a bit) or Lookout for mobile devices. Azure AD will then determine whether to block or allow the device to utilize the corporate resources or not. In addition, you can also configure Intune to help deploy software updates to Windows 10 as needed.
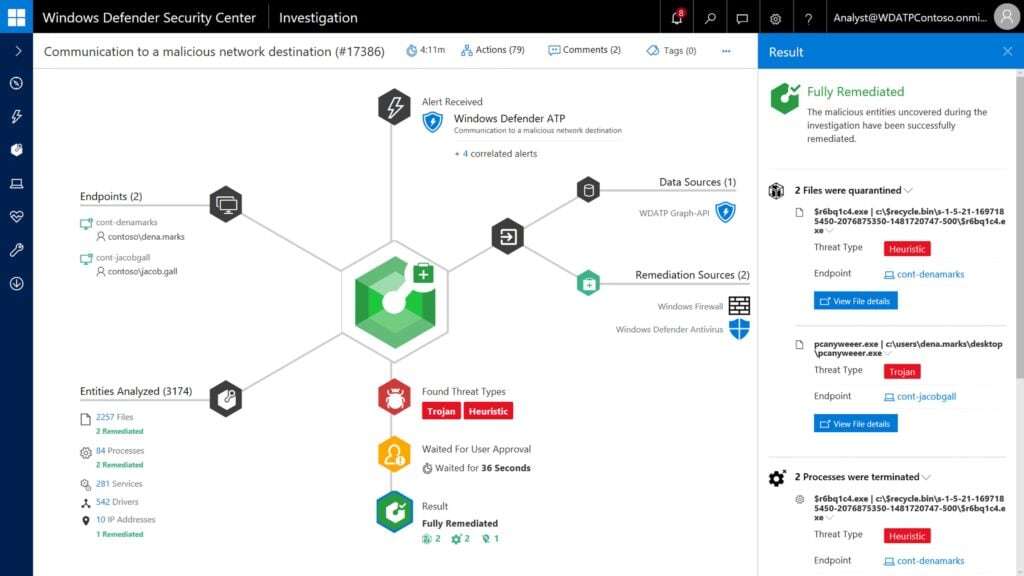
Microsoft Defender ATP is Next-Gen Anti-Virus
Much like firewalls, conventional anti-virus is no longer as effective as needed to provide corporate defense against malware. However, Microsoft is ready to provide a modern solution. Microsoft Defender Advanced Threat Protection (MD ATP) (formerly Windows Defender ATP) provides next-gen anti-virus protection against modern ransomware. MD ATP combines the following concepts to protect against modern threats:
- intelligence-driven protection
- post-breach detection
- automated investigation
- response orchestration
Microsoft Defender ATP is powered by behavioral sensors, analytics, and machine learning, to combat and mitigate breaches in unique ways. For example, in order to keep breaches from spreading, it will automatically isolate any machines that are compromised. This avoids problems that malicious actors use like pass-the-hash attacks to extract user credentials from compromised devices. In addition, Microsoft Defender ATP creates a risk level so system administrators know when and why a device was blocked.
Providing Cloud Security
One of the primary concerns when it comes to modern cybersecurity is the cloud. There are many benefits to businesses moving to the cloud, but there are also concerns that security isn’t moving fast enough to try and address potential problems. Microsoft 365 is at the front of the line in terms of providing added cloud security. Microsoft Cloud App Security provides essential shadow IT support by identifying all cloud apps and services in use from a list of 20,000 vendors, and assigns a risk rating to them so you can manage them accordingly.
Cloud App Security can also take a more active role, if you need it. For example, CAS can monitor and block access to Sharepoint, Google Drive, Box and Salesforce if it detects abnormal activity. In addition, Microsoft’s catalog of 20,000+ applications includes compliance data for regulations such as ITAR, HIPAA, FINRA, SOC1, SOC2, NIST 800-53, ISO 27001, FedRAMP, SOX, and many more.
Closing Thoughts on Zero Trust Security Concepts
Zero trust security concepts are something that everyone can make use of, especially businesses that hold sensitive data. While making the change can seem intimidating, Microsoft has done a lot to forward the idea of zero trust security solutions. This is accomplished by putting out a suite of products that can be easily integrated into your security workflow at an affordable price for any size organization, such as Azure Active Directory.
If you need help implementing zero trust security concepts for your environment, or have more questions about how to effectively implement tech solutions in your business, we’re happy to help at Infused Innovations. Our goal is to help all companies integrate the changes and advancements they need to compete in a world of rapidly changing technology. Whether you want to implement some or all of the above features, we can help make it happen. Reach out to us to schedule a Zero Trust Security Acceleration workshop today.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
MAM and Intune: Sandboxing Corporate Data

Forrester Ranks Microsoft a Leader in Cloud Security Gateways

No Comments Yet
Let us know what you think