Go Passwordless With Microsoft 365
Using SMS for MFA and resetting passwords every 90 days is a losing game. People write passwords on sticky notes, and your phone carrier will let hackers port your phone number to a new SIM card. Going passwordless with biometric unlocks is the only way forward. Your phone can unlock with your fingerprint or FaceID, and so can Windows 10. Windows Hello is included in all Microsoft 365 SKUs and allows your users to go passwordless by signing in with their face, thumbprint, or PIN.
Adopting modern authentication technologies will allow your new security measures to blend seamlessly into a user's everyday workflow. The best technologies are the ones that are so transparent, your users don't even know they are there.
Going Passwordless with Microsoft 365
I've caught glimpses of employees write down various passwords to help remember them. After all, they needed to have sixteen characters, a combination of upper- and lower-case letters, numbers, and special characters, and each one needed to be unique. One colleague went to an extreme and never actually wrote down the passwords themselves, but devised a system of codes. "Password #1b," "password #2 third update added characters less one number," etc. And for added security these reminder notes needed to be stored in separate, inconspicuous locations: the filing cabinet, under the keyboard, the office windows. Hello! It was enough to motivate me to go password-less for them!
For the past few years, Microsoft has been developing a four-step process which removes more and more of the vulnerability in logging into services and apps. These steps are:
- Develop password-replacement offerings -- enable Microsoft Authenticator or Windows Hello in your Office 365 tenant.
- Reduce the surface area of passwords -- integrate third-party applications using SAML 2.0 with Azure Single Sign On (SSO). Then enable seamless single sign on to automatically sign in users with their Azure AD account.
- Transition to deployment without passwords -- users never use their password and do not even need to remember them.
- Eliminate passwords from the identity directory -- passwords no longer exist at all.
And what doesn't exist can't be stolen.
I upgraded to build 1903 of Windows 10 a few weeks ago, which offers FIDO2-certified alternative login options via Windows Hello so I don't have to use a password anymore. That means that if you're one of the 800 million people who use Windows 10, your life could get this much easier too. What's even more exciting is that I can use Windows Hello to sign into my Windows Virtual Desktop (WVD) instance in Azure now too! Deployment of Windows Hello with the new Cloud Trust method makes setup much easier too.
What is Windows Hello?
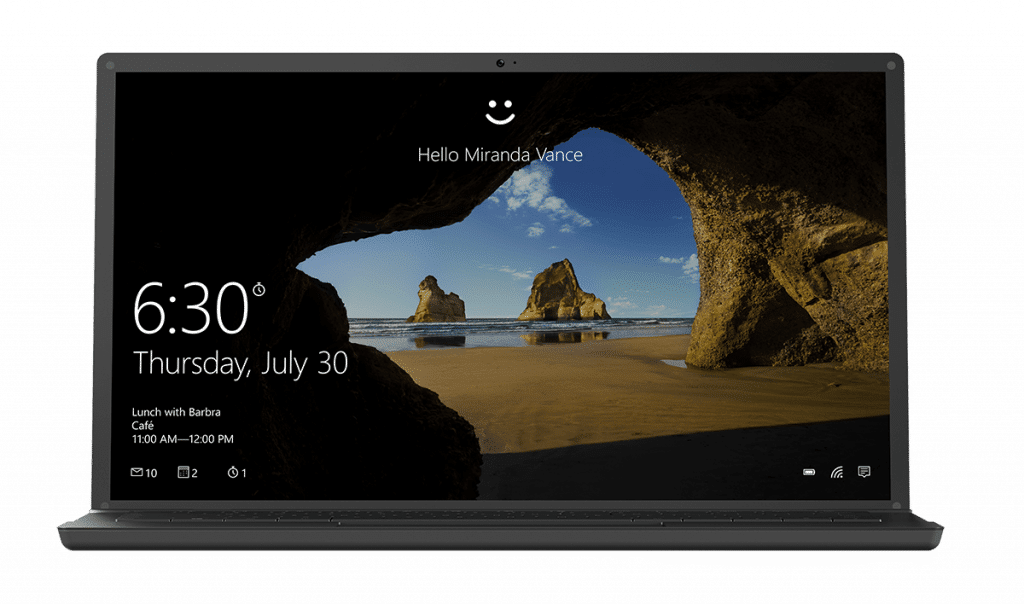
Microsoft is a leading member of the FIDO Alliance. So it's not surprising that they now offer a login method that uses infrared facial recognition or fingerprints to authenticate. It instantly signs users into any type of device with no password necessary. And with Windows 10 1903, it can be used for app logins as well. For those who change their hair or makeup style often and fear their device camera's inability to recognize them, rest assured that the false rejection rate is less than 10% and a PIN can be kept for backup. When identical twins tried to break Windows Hello as a test, they couldn't. Personally, I require a multifactor unlock so I must enter a PIN with a biometric authentication at logon. I recommend this to all of my clients with NIST compliance requirements as well.
Using the Microsoft Authenticator App for Passwordless Login
Microsoft Authenticator is available on iOS and Android devices. Signing into Azure AD using passwordless authentication is currently in public preview and configuration steps are available here:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-enable
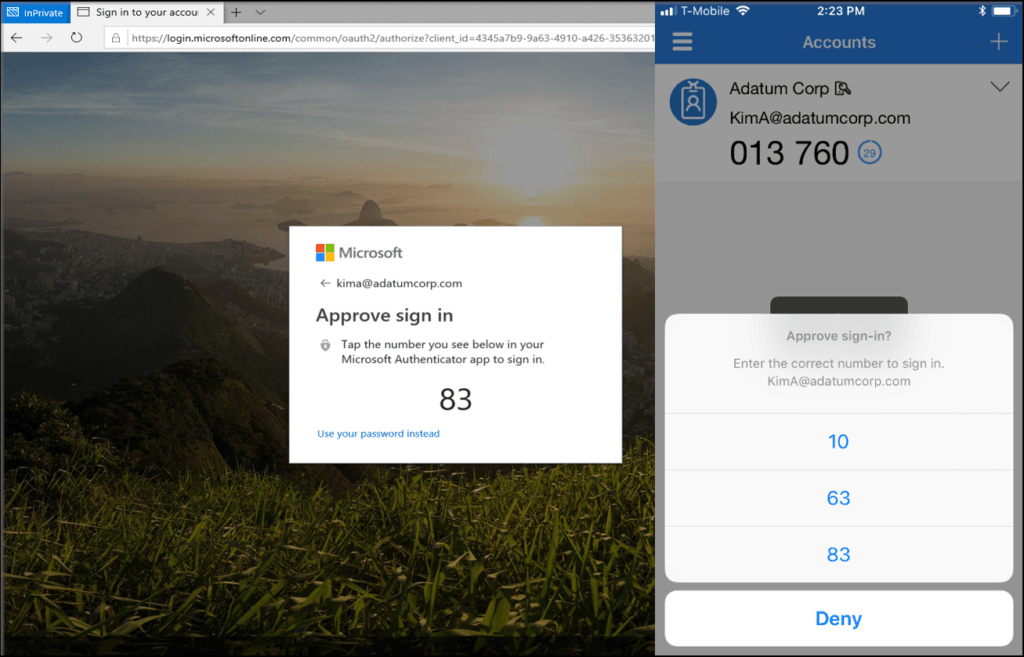
The Authenticator app has been great for MFA challenges for years, but last year at Ignite, Microsoft announced the new passwordless sign on experience shown above.
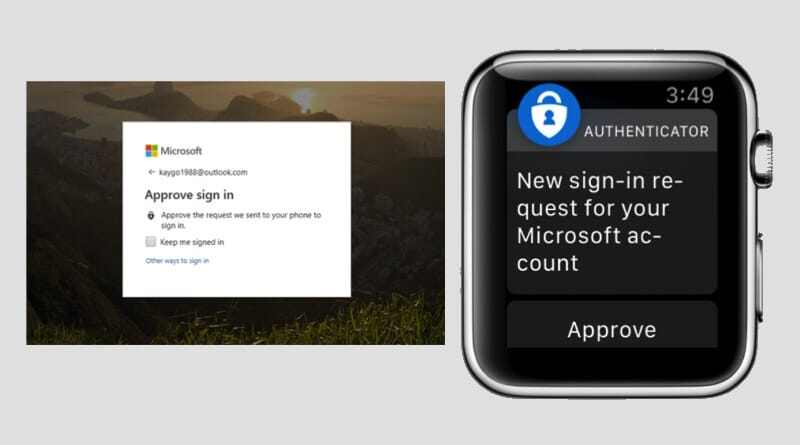
I love the MFA experience on the Apple Watch with Microsoft Authenticator, pictured above. It's very Pavlovian when I get the vibration alert on my watch to confirm an MFA challenge. It provides a positive haptic response that I'm signing in securely, instead of dreading sitting through a phone call or memorizing the verification code in a text message that I need to retype. And it's more secure too since I can only approve the sign in if I'm wearing the watch.
What is FIDO2?
Studies show that every day, humans collectively spend 1,300 years entering passwords onto their devices. A stunning majority of these passwords are weak and too vulnerable to phishing or theft. The FIDO Alliance is dedicated to eliminating this security problem by phasing out passwords altogether, using biometrics or PINs instead. FIDO2 refers to the Alliance's newest set of specifications, namely the World Wide Web Consortium’s (W3C) Web Authentication (WebAuthn) specification and the corresponding Client-to-Authenticator Protocol (CTAP). This certified technology allows users to quickly and easily authenticate to online services on any kind of device.
Members of the FIDO Alliance include many well known brands:

FIDO2 keys can be purchased for any existing computer. Yubikey offers a FIDO2 key, but it doesn't have a fingerprint scanner on it. This means if you lose the Yubikey, you've also lost your identity. I only recommend Yubikeys for multifactor unlock scenarios. My preference are the Biopass FIDO2 keys by Feitian, which include fingerprint scanners:
- https://shop.ftsafe.us/collections/fido2/products/k24
- https://shop.ftsafe.us/collections/fido2/products/k26
- https://shop.ftsafe.us/collections/fido2/products/k27
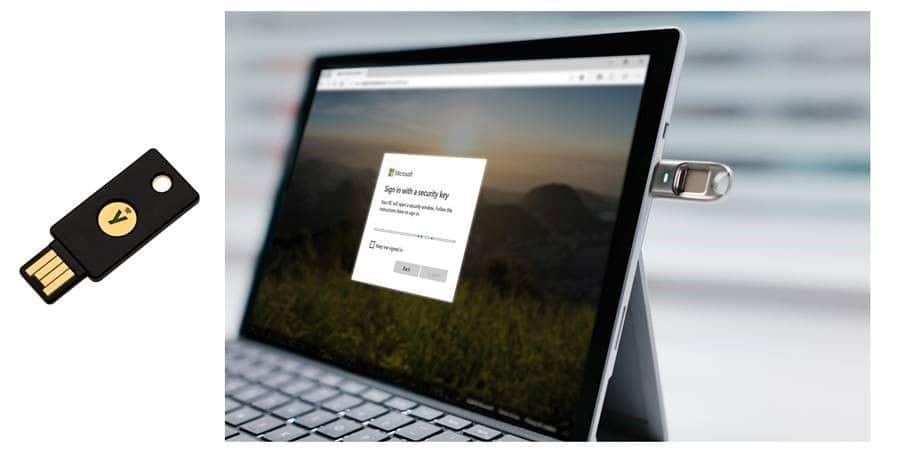
However, Android 7.0+ recently announced FIDO2 support for their operating system. In the near future, you may be able to use NFC with your phone to login too!
Closing Thoughts on Going Passwordless with Microsoft 365
I hate passwords. If an application doesn't support FIDO2, SAML with Azure SSO, or Windows Hello then I don't use it. I stopped using Macbooks years ago because they don't have biometric unlocks built into their hardware. Why FaceID isn't on any of their workstations is beyond me. (I'm looking at you, Andy!) (Andy is my brother that designs the logic boards for Macbooks at Apple.)
In the past, certificate based authentication was the seamless way to provide passwordless sign-on for your users. With Windows Hello and Microsoft 365, you can easily deploy passwordless sign on to all of your users via Intune and without having to maintain an expensive Private Key Infrastructure (PKI). Now with FIDO2 being officially adopted this year, going passwordless is no longer in the future. Passwordless login is here now and it's ready for commercial adoption.
Stay connected. Join the Infused Innovations email list!
Share this
You May Also Like
These Related Posts
Get Your Organization Ready to Leave Passwords Behind

Let's Face It: Passwords Aren't Secure Enough for Your Business

No Comments Yet
Let us know what you think