Posts by Dan Chemistruck
Microsoft’s Windows Defender AV Earns “Top Product” Award in June 2019 Antivirus Comparison
Microsoft’s Windows Defender AV just received the top score and “Top Product” award from the independent German institute, AV-Test. Wow, that’s not something you hear very often! In fact, one of the most common statements that we hear when discussing cloud security with Microsoft 365 is: “Microsoft made the security abomination that is Windows XP,…
Read MoreGo Passwordless With Microsoft 365
Using SMS for MFA and resetting passwords every 90 days is a losing game. People write passwords on sticky notes, and your phone carrier will let hackers port your phone number to a new SIM card. Going passwordless with biometric unlocks is the only way forward. Your phone can unlock with your fingerprint or FaceID,…
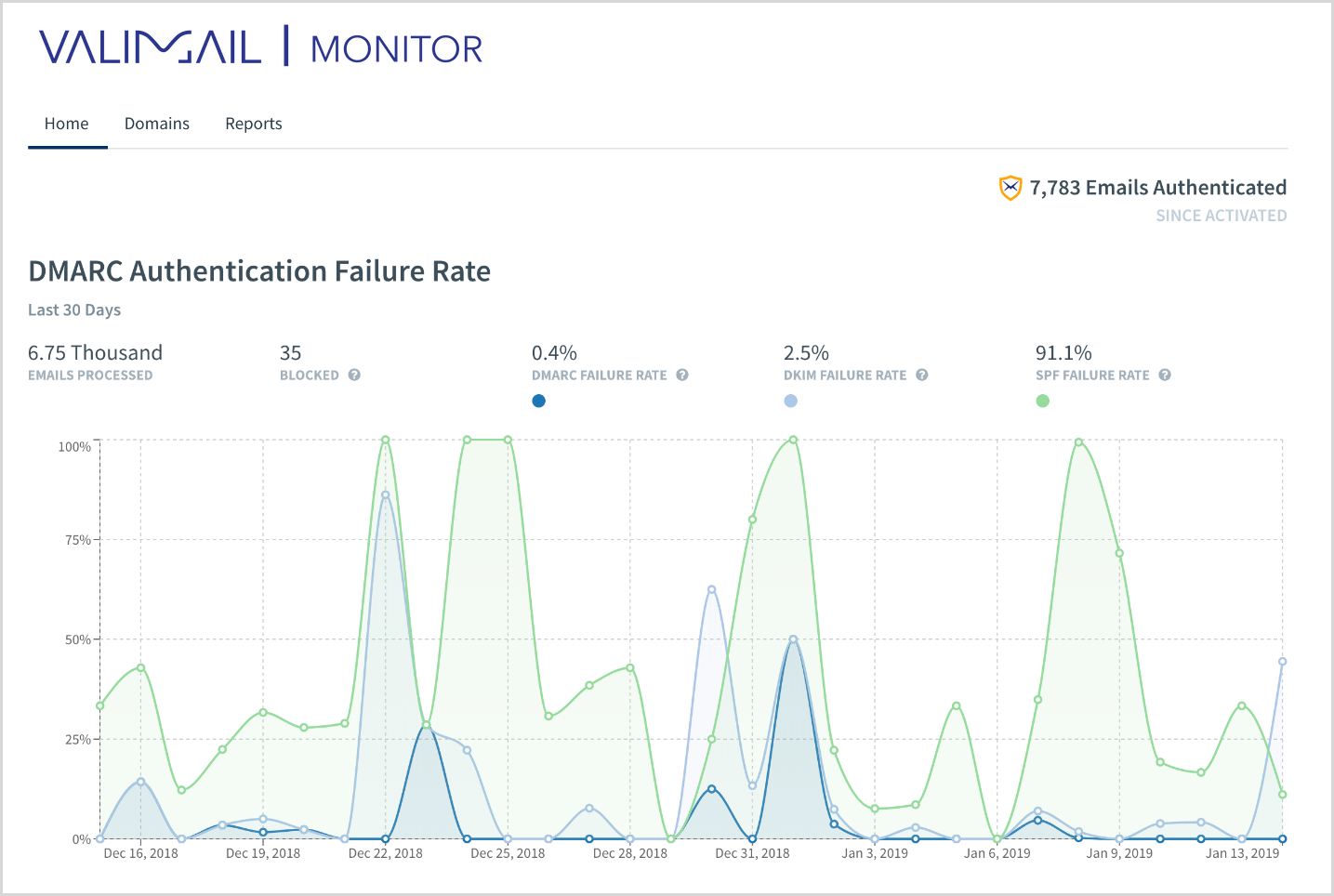
Read MoreStep-by-Step Guide to Configure Valimail for DMARC Monitoring With Office 365 and Azure SSO
Last month, Microsoft announced that anyone with an active Office 365 subscription can configure Valimail for DMARC monitoring for free! Great! But what the heck does that mean? In simple terms, it means you can eliminate 40-70% of phishing and spoofing attacks on your domain, and you’re going to help make the Internet a safer…
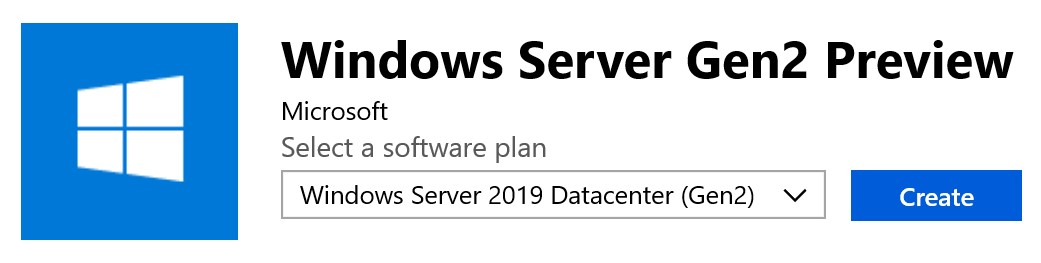
Read MoreGuide to Deploy Gen2 VMs in Azure
This week Microsoft announced the public preview of support to deploy gen2 VMs in Azure. Gen2 VMs have been around since Windows Server 2012 R2 for on-premises Hyper-V deployments. However, there are some serious limitations during the Azure preview. Let’s look at the benefits first. Why Should I Deploy Gen2 VMs in Azure? For security…
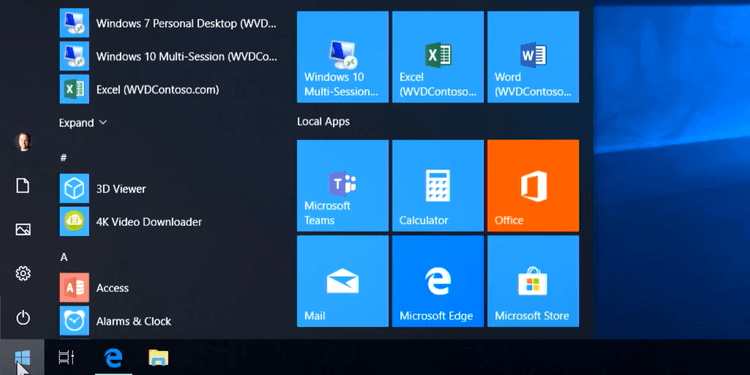
Read MoreGuide to Deploy Office 365 ProPlus in Windows Virtual Desktop
I deployed Windows Virtual Desktop (WVD) four times the day it came out and shared my thoughts about it. One of the first questions I received was how to deploy Office 365 ProPlus in Windows Virtual Desktop. That’s because if you run the web installer on any multi-user computer with Terminal Services, you’ll receive the…
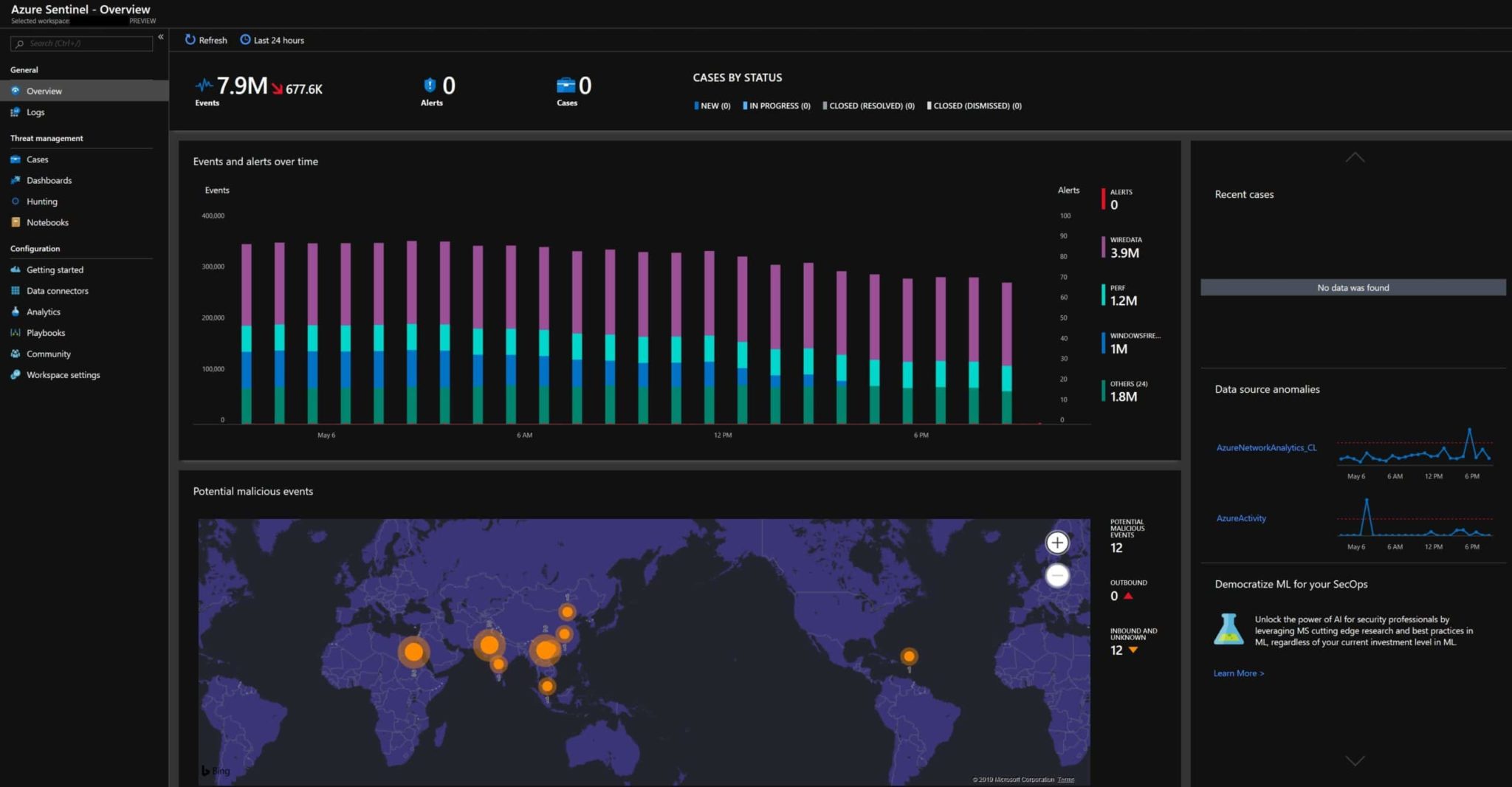
Read MoreStep-by-Step Guide to Deploy Microsoft Sentinel
Note to readers: this guide was created in 2019 and is being kept online as an example of the process. The product (now Microsoft Sentinel) has evolved over the years, and a well-built, best-practice deployment is not a “15 minute guide” level of effort. Please reach out to us if you’re interested in using Sentinel…
Read MoreInfused Innovations Earns Microsoft DevOps Gold Competency for their Azure DevSecOps Platform: Infused Threat Protection
We are proud to congratulate the Infused Innovations engineering team for their continued demonstration of expertise across the Microsoft cloud ecosystem. As Infused Innovations expands its service offerings into new areas, we have taken a three-pillar approach to our internal processes: automate for agility & consistency, deploy to the cloud for availability, and make sure…
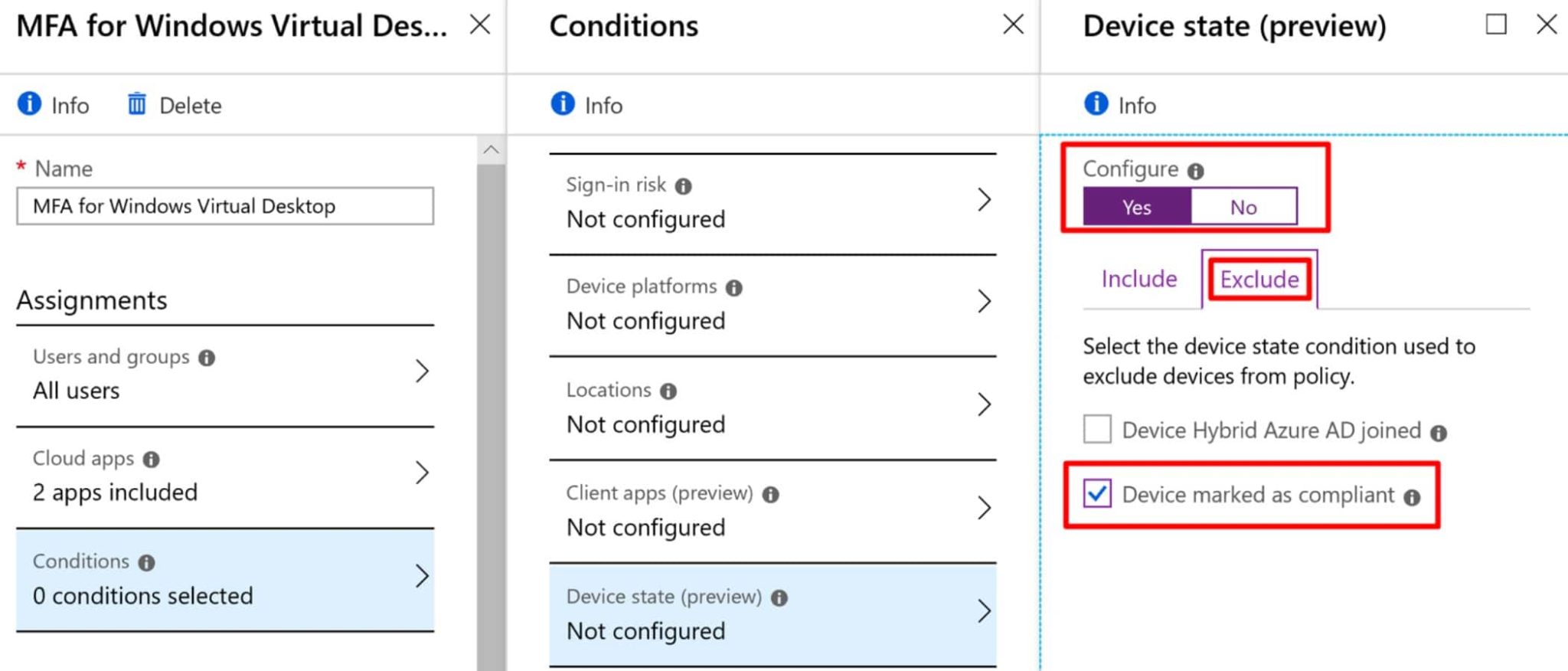
Read MoreStep-by-Step Guide to Securing Windows Virtual Desktop in Azure with Conditional Access and MFA
One of my biggest complaints about using Azure AD P1 to issue Azure MFA challenges on a traditional RDS deployment via RADIUS authentication is that it issues an MFA challenge on every login. That’s almost as frustrating as trying to understand Microsoft Licensing. Fortunately, securing Windows Virtual Desktop in Azure with Conditional Access and MFA…
Read MoreStep-by-Step Guide to Deploy Windows Virtual Desktop in Azure
Windows Virtual Desktop (WVD) was finally released to public preview GA (UPDATED 9/2019), so here’s your step-by-step guide to deploy Windows Virtual Desktop! For those of you that have been living under a rock (or spending time with your friends and families), WVD is Microsoft’s new Desktop-as-a-Service offering to provide Windows 10 virtual desktop infrastructure…
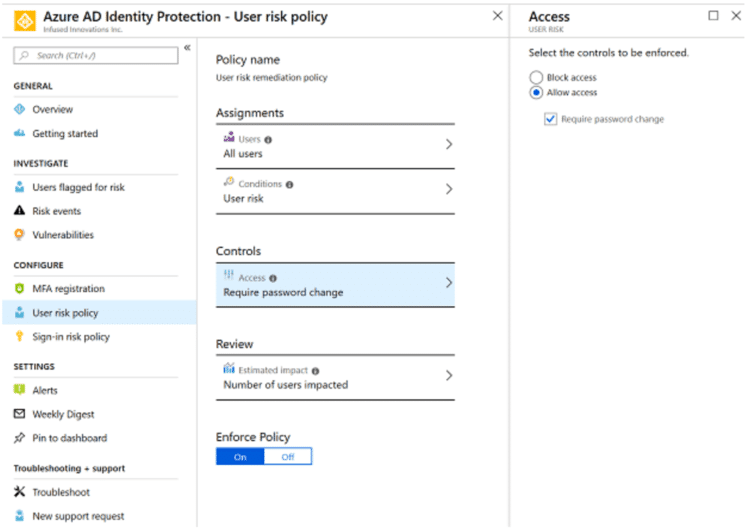
Read MoreThreat Hunting with Azure AD Premium Subscriptions
Every cloud security workshop that I perform with a client to enable Microsoft’s Enterprise Mobility + Security (EM+S) suite typically yields an unpleasant surprise. I had the CFO of one company demand the immediate implementation of Roles Based Access Control (RBAC) after seeing the granularity of the audit capabilities of Cloud App Security. During my…
Read More