Your Zero Trust Roadmap
Zero Trust security with multiple vendors has zero chance of success. Our cybersecurity experts will help you consolidate your security portfolio onto the Microsoft Defender XDR stack with product mapping sessions and proof of concept deployments.
Accelerate Your Zero Trust Journey With Our Rapid Onboarding Framework for Microsoft 365 Defender
Zero Trust Security Accelerators
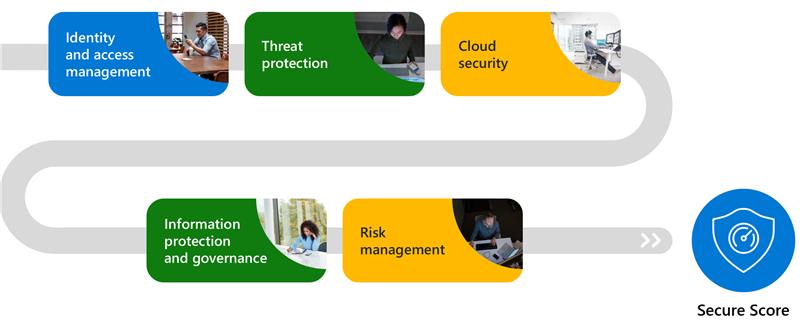
Built On Six Pillars of Zero Trust

Identities
Verify and secure each identity with strong authentication across your entire Digital Estate.

Endpoints
Gain visibility into devices accessing the network. Ensure compliance and health status before granting access.

Apps
Discover shadow IT, ensure appropriate in-app permissions, gate access based on real-time analytics, and monitor and control user actions.
Data
Move from perimeter-based data protection to data-driven protection. Use intelligence to classify and label data. Encrypt and restrict access based on organizational policies.

Infrastructure
Use telemetry to detect attacks and anomalies, automatically block and flag risky behavior, and employ least privilege access principles

Network
Allow access to resources based on a strongly authenticated identity, ensuring resource access is verified in real-time.
Managed Cloud Security
Stop Ransomware & Stay Current Against New MITRE ATT&CKs
Infused Threat Protection
End-to-End Modern Cybersecurity Management











