Cloud Security
Top Microsoft Announcements at RSA 2020
The security-centric RSA Conference kicks off this week in San Francisco. Following the conference news is a great way to stay updated about the latest security developments being offered in technology. Let’s take a look at the exciting top Microsoft announcements at RSA 2020. Note: RSA was just purchased by the Symphony Technology Group last…
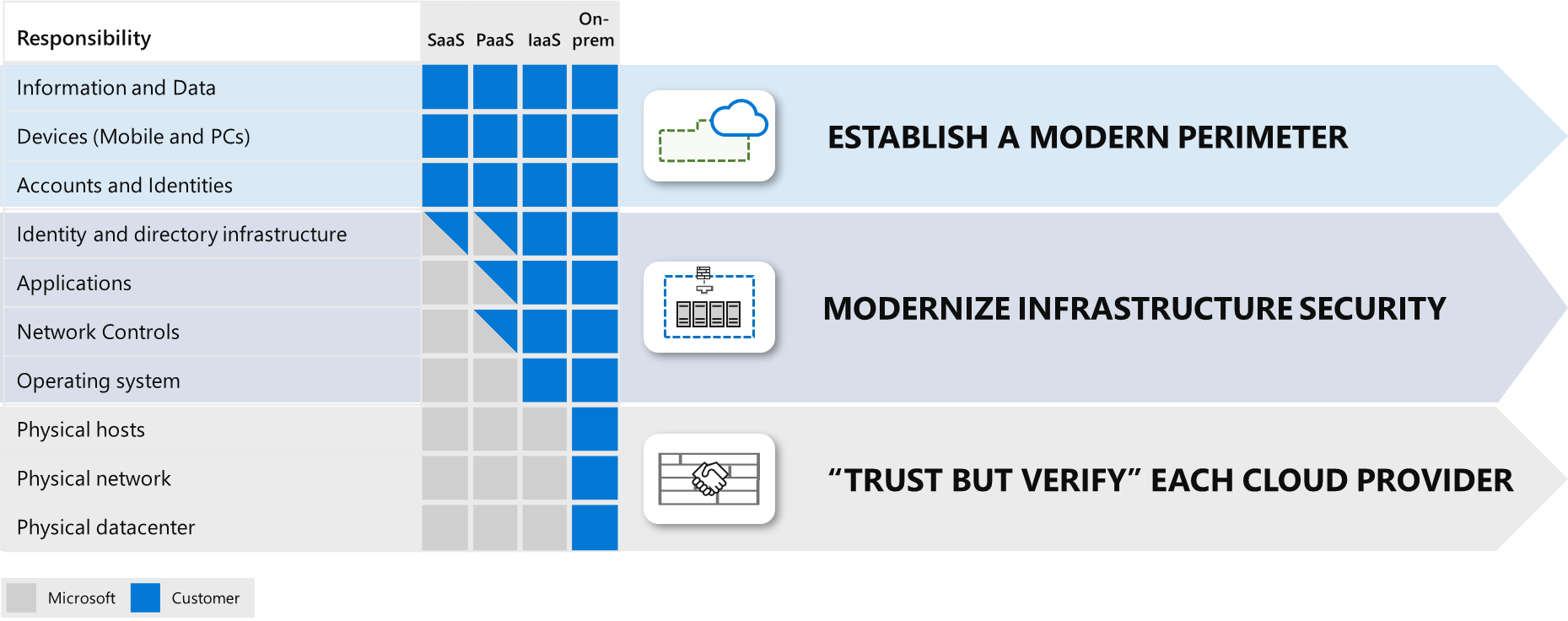
Read MoreShared Responsibility Matrix for Cloud Services
When migrating to the cloud, organizations sometimes mistakenly assume that the cloud service provider (CSP) takes on the role of securing their data and maintaining compliance. While the CSP does have many responsibilities in these areas, it’s important to remember that the customer is also responsible. The service model you choose dictates your accountability in…
Read MoreFinancial Cybersecurity for Modern Hacks on World Banks
We hear about a large world bank hack almost every week these days. From the recent Capital One breach to the European Central Bank attack, how can you trust that your bank is safe? The financial industry must follow a number of compliance frameworks on their IT systems to secure and protect data. Unfortunately, we…
Read MoreMicrosoft’s Windows Defender AV Earns “Top Product” Award in June 2019 Antivirus Comparison
Microsoft’s Windows Defender AV just received the top score and “Top Product” award from the independent German institute, AV-Test. Wow, that’s not something you hear very often! In fact, one of the most common statements that we hear when discussing cloud security with Microsoft 365 is: “Microsoft made the security abomination that is Windows XP,…
Read MoreZero Trust Security Concepts and Microsoft 365
88 records were lost or stolen every second in 2017, and that number is only likely to increase. The two most common settings for these breaches to take place are healthcare and banking as a distant second. As companies move to ensure their entire supply-chain is compliant to meet strict regulations, such as GDPR and…
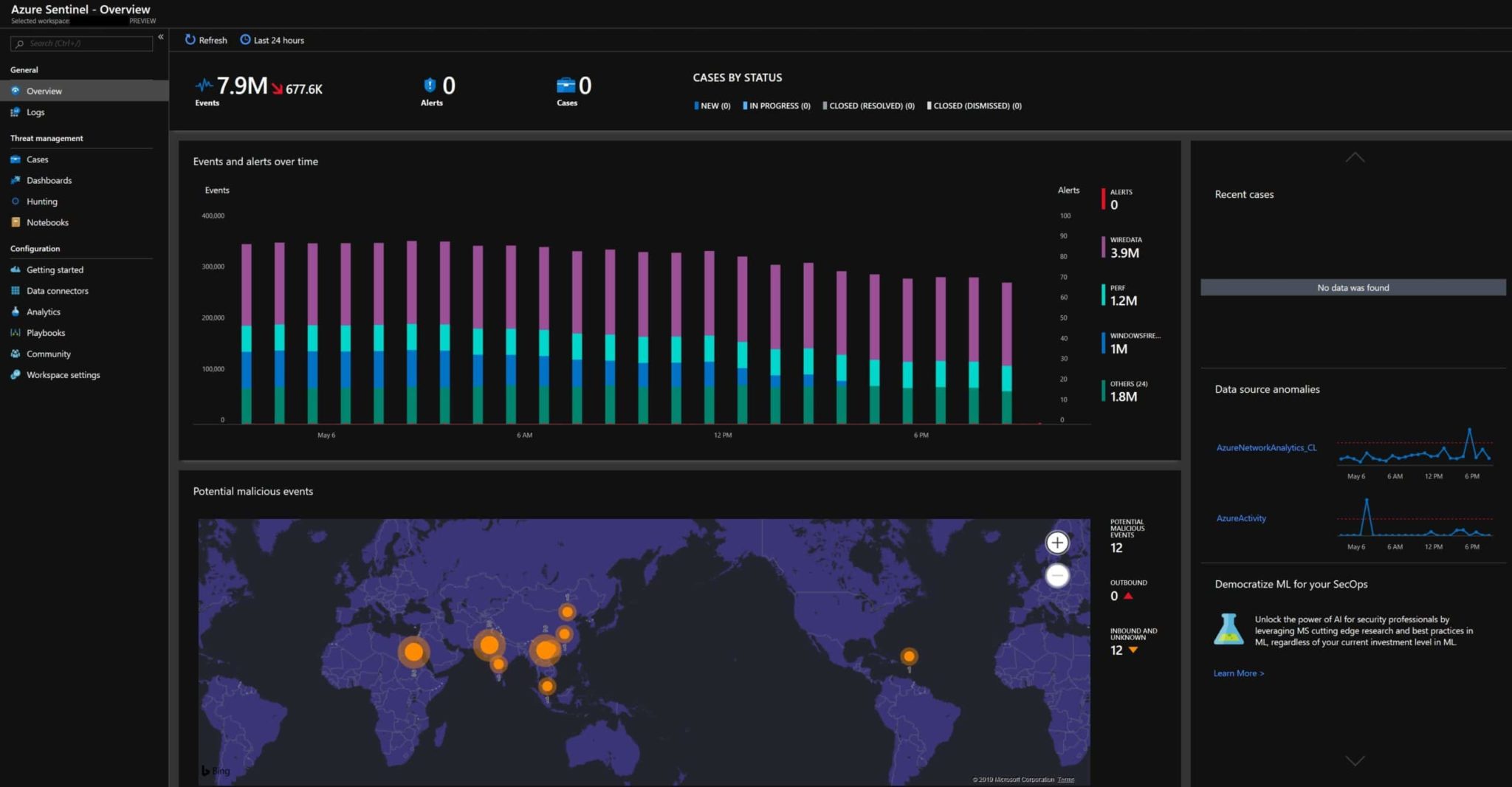
Read MoreStep-by-Step Guide to Deploy Microsoft Sentinel
Note to readers: this guide was created in 2019 and is being kept online as an example of the process. The product (now Microsoft Sentinel) has evolved over the years, and a well-built, best-practice deployment is not a “15 minute guide” level of effort. Please reach out to us if you’re interested in using Sentinel…
Read MoreInfused Innovations Earns Microsoft DevOps Gold Competency for their Azure DevSecOps Platform: Infused Threat Protection
We are proud to congratulate the Infused Innovations engineering team for their continued demonstration of expertise across the Microsoft cloud ecosystem. As Infused Innovations expands its service offerings into new areas, we have taken a three-pillar approach to our internal processes: automate for agility & consistency, deploy to the cloud for availability, and make sure…
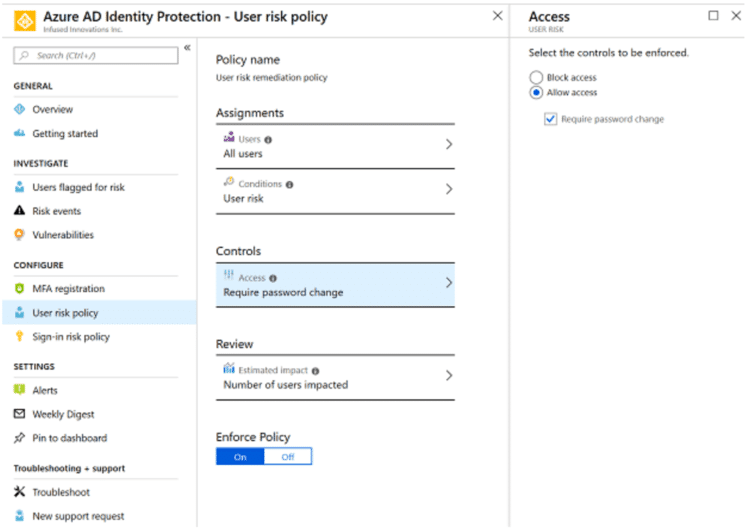
Read MoreThreat Hunting with Azure AD Premium Subscriptions
Every cloud security workshop that I perform with a client to enable Microsoft’s Enterprise Mobility + Security (EM+S) suite typically yields an unpleasant surprise. I had the CFO of one company demand the immediate implementation of Roles Based Access Control (RBAC) after seeing the granularity of the audit capabilities of Cloud App Security. During my…
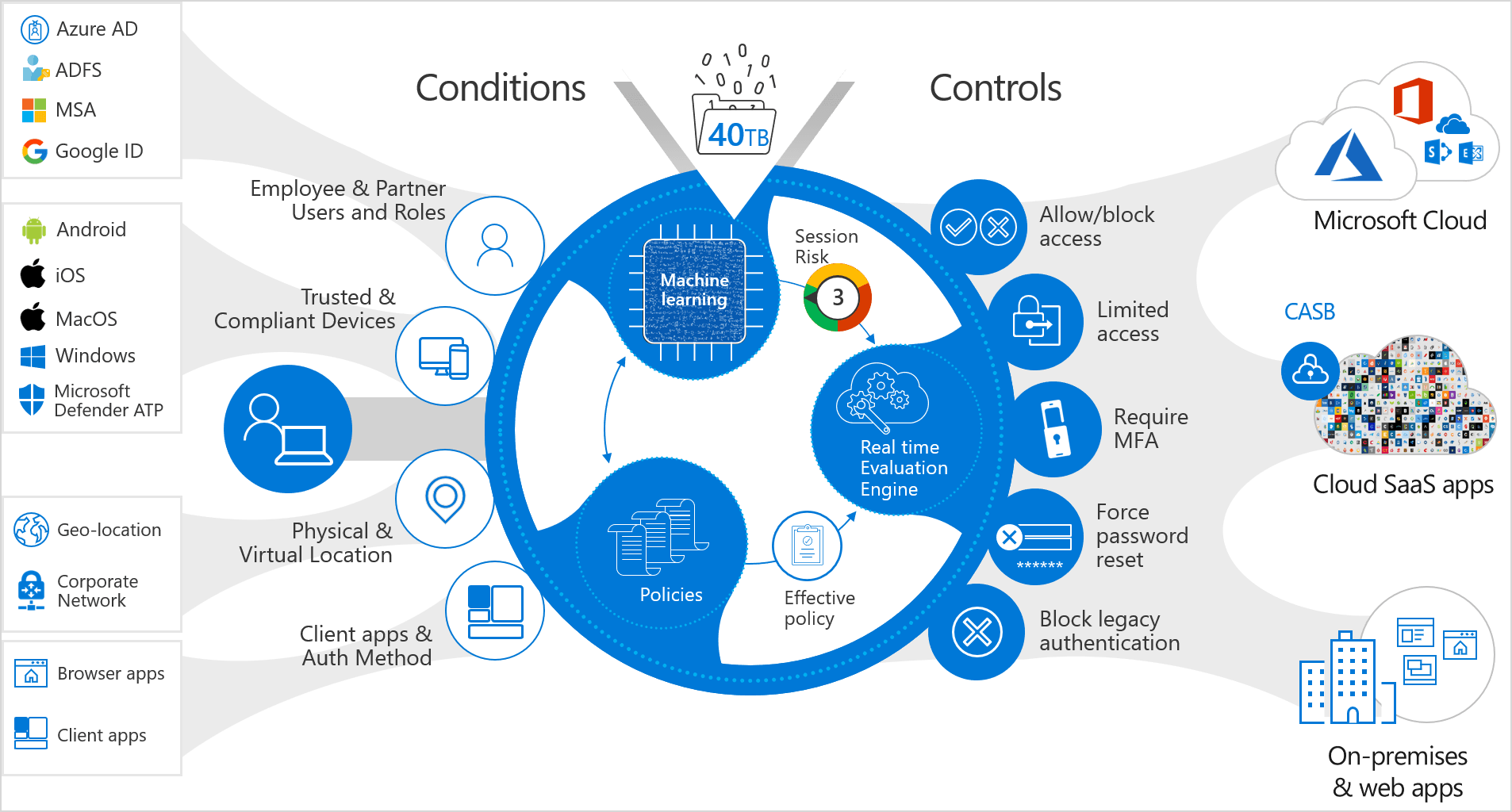
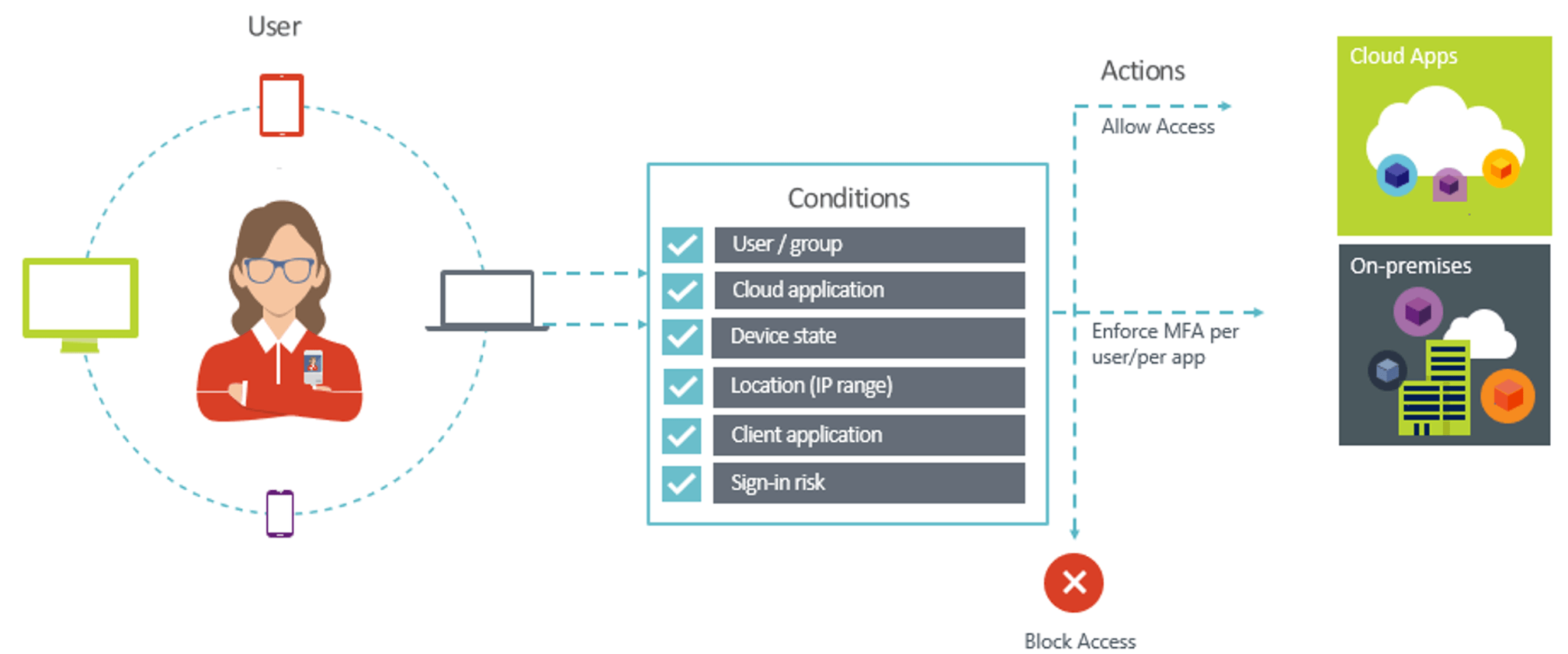
Read MoreBetter together: Conditional Access with Azure MFA (Multifactor Authentication)
As enabling multifactor authentication is the number one security recommendation to improve your Microsoft Secure Score, let’s take a look at why it’s better to deploy Conditional Access with Azure MFA together. We’ll walk through deploying Azure MFA for all of your users in a single day and most users won’t even notice! Isn’t Office…
Read MoreYou’re on the Wrong Microsoft 365 License for your Business
Well, you’re probably on the wrong Microsoft 365 business license. If you’re on one of the following plans, then skip this article: Microsoft 365 E5 Microsoft 365 E3 plus Microsoft 365 E5 Security (Previously called Identity Threat Protection) Microsoft 365 Business plus Azure AD P2 But if you’re like most organizations that we speak to,…
Read More