
Identify Sensitive Data and Risks in Your Organization with a Compliance Accelerator
Many companies today handle sensitive data and private information, and they therefore carry increased risk in the event of a data breach. It’s crucial to identify sensitive data and risks that come with that data, for good business practice as well as legal compliance. That’s not necessarily an easy thing for organizations to do, though. Our Compliance Accelerator series helps businesses walk through the steps of managing their data in smart ways that ensure good legal standing. The first step is to build an Information Governance Strategy; once that’s laid out, you can learn about the sensitive data and risks that your company is dealing with. That’s where this second Compliance Accelerator becomes very helpful.
Objectives of the Compliance Accelerator to Identify Sensitive Data and Risks
When undertaking this Compliance Accelerator, we’ll work with your team to meet these objectives:
- Understand the risks of Dark Data: As Gartner points out, at companies all over the place “employees are blindly building a bottomless lake of data.” This is all of the files, emails, web content, etc. that are saved just in case but never get used. As this data pile is often overlooked, there could be information there that puts your organization at risk without team members realizing it.
- Discover privacy and regulatory risks of existing data: We’ll help you figure out where you have private information and ways your organization may be non-compliant.
- Assess the Microsoft 365 environment: Our Compliance Accelerators are for businesses using Microsoft 365. We’ll check against a set of controls for key regulations as well as standards for data protection and general data governance to evaluate your environment.
- Analyze and report: We’ll analyze what we find and explain it to you, highlighting the most impactful elements and providing insight on how they can affect you.
- Recommendations and next steps: We’ll guide you through recommendations for actions based on your particular scenario.
- Learn about tools and services that can mitigate risks: The tools that address these risks can seem confusing to company leaders, so we’ll explain how they work and make sure you understand processes related to your sensitive data.
Data Risk Check
When we do your data risk check, we will enable the services for automated discovery, configuring the search artifacts to find your risk areas. We’ll allow automated discovery to run for several days to search for privacy and regulatory risks in organizational data. It will find where you have the following risks: sensitive information; stale data such as old documents and emails that no longer have business value; and any risky activity that may have occurred, like copying sensitive data to USB drives or other uncontrolled locations.
Only Microsoft-hosted environments will be checked—other cloud services such as Google or AWS are not within the scope of this accelerator. The locations that will be searched include Exchange Online, Sharepoint Online, and Microsoft Teams. You’ll have the option to search additional places as well.
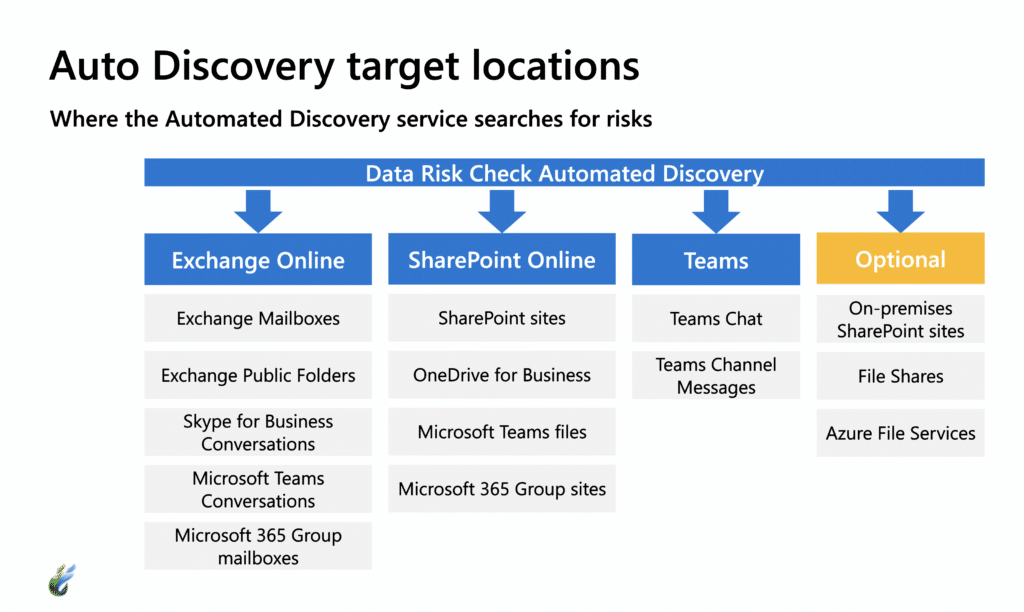
Once automated discovery is finished, we’ll analyze the findings and report the identified privacy and regulatory risks to you.
Compliance Manager Tenant Assessment
Also included in this Compliance Accelerator is an assessment through Compliance Manager. This will measure your performance relative to key data protection standards and regulations, generating a score for how well your business is currently doing in regard to compliance. We’ll walk you through what your compliance score means and how you can improve it.
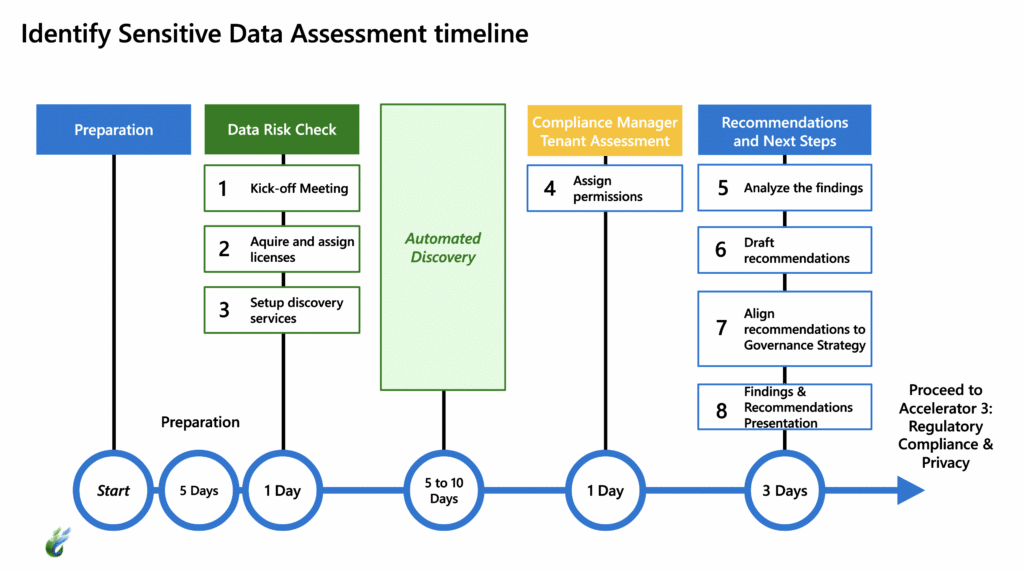
Once you’ve learned where you’re at in terms of sensitive data, risk, and compliance score, we can guide you through implementing your plan to address these issues. The following Compliance Accelerator is for Satisfying Regulatory Compliance & Privacy Requirements.
